|
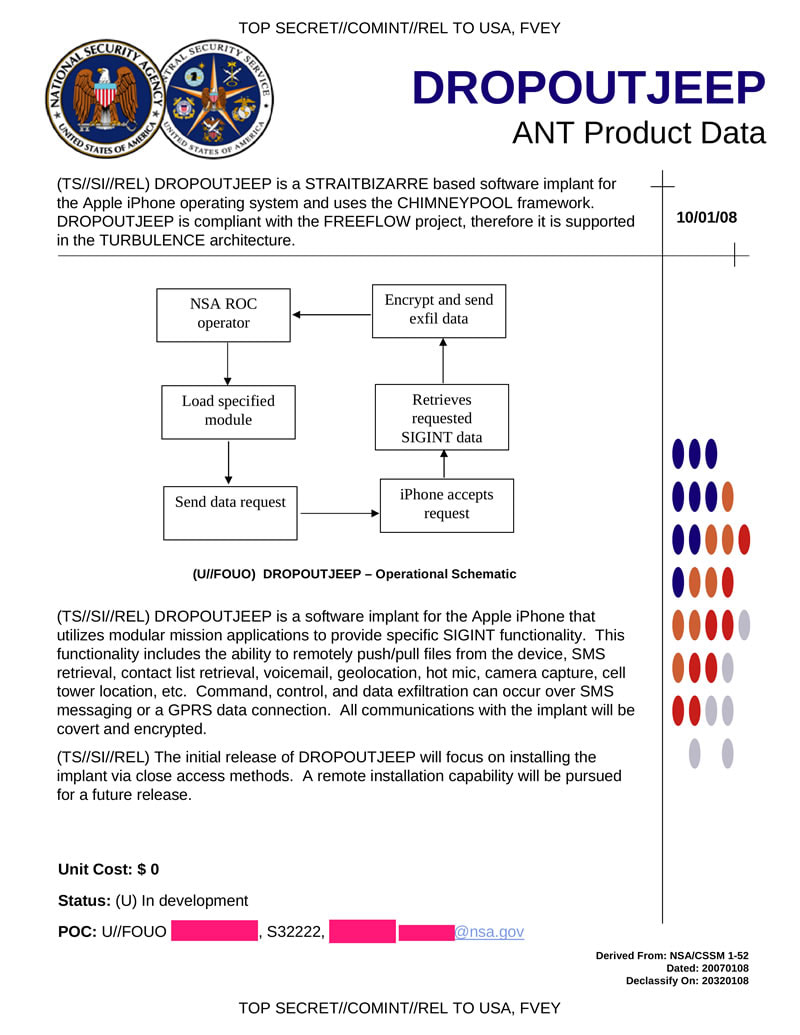
If you haven't already been informed, the new iPhone X was announced September 12, 2017. While the $1,000 device represents a whole new era of technological achievement, many of the new capabilities should raise some concern. Most notable is Face ID; the ability to unlock the device with the user's face and eyes. This feat is accomplished by a number of new sensors built into the front-facing screen, including a dot projector, infrared camera, flood illuminator and proximity sensor. By projecting a field of over 30,000 invisible dots out into the environment, together these sensors are able to constantly scan for and map the geometry of the user's face to unlock the device from multiple angles, even in the dark. In other words, your face is your password. The technology is able model faces and adapt to the changing landscape and aspects of a person’s face as they grow and change. Apple states that the biometric data is stored locally on the device and claims that Face ID cannot be fooled by photographs of faces. Beyond the obvious question, "why is this necessary?", delving deeper into the device and it's data ties with the intelligence agencies, should raise skepticism regarding the true intentions behind the technology. Privacy Violation: Governments Spying Via iPhones According to hundreds of leaked documents via Wikileaks, as many as 160 intelligence contractors in the mass surveillance industry may have access to the data on a single cellular device. Intelligence agencies, military forces and police authorities are able to silently, and on mass, and secretly intercept calls and take over computers without the help or knowledge of the telecommunication providers - no matter the country. Users’ physical location can be tracked if they are carrying a mobile phone, even if it is only on stand by. In addition, systems to infect every Facebook user, or smart-phone owner of an entire population group are and have been on the intelligence market since the rise of the patriot act, due to events that took place on September 11, 2001. Companies like Phoenexia in the Czech Republic collaborate with the military to create speech analysis tools. These speech analysis tools are able to identify individuals by gender, age and stress levels and track them based on ‘voiceprints’. DROPOUTJEEP, a spyware said to be one of the tools employed by the NSA's ANT (Advanced or Access Network Technology) division, is able to gain backdoor access to various electronic devices. DROPOUTJEEP can infiltrate virtually all areas of the iPhone (not only the iPhone X), including voice mail, contact lists, instant messages, and cell tower location. The general response among people who have justified and have been normalized to privacy violation after reading this is, "I have nothing to hide." Why is it that one closes the door when they use the restroom? Or why does one have a password on their phone is the first place? Akin to freedom of speech, privacy is, or should be, a basic human right. But the reality is that the right to privacy no longer exists. By waiving your freedom of privacy and saying, "I have nothing to hide", is equivalent to waiving your freedom of speech and saying, "I have nothing to say." Normalizing Facial Scanning Have you had your fingerprints taken for government ID? Your irises scanned? Your earlobes measured? A microchip implanted? Are you prepared to? Where will you draw the line? Acknowledged or not, this technology is normalizing facial scanning. Let us not be naive, this is a coordinated plan to institute a worldwide biometric id system to track every human on the planet. Faces Contain a Significant Amount of Data The science of judging one’s character from their facial characteristics, or physiognomy, dates back to ancient China and Greece. Aristotle and Pythagoras were among its disciples, and the latter used to select his students based on their facial features. Cesare Lombroso, the founder of criminal anthropology, believed that criminals could be identified by their facial features. There is a growing body of evidence suggesting that character can influence one’s facial appearance, and vice versa. The appearance of an individual's face drives first impressions of others, influencing our expectations and behavior toward them, which, in turn, shapes their character. The existence of such links between facial appearance and character is supported by the fact that people can accurately judge others’ character, psychological states, and demographic traits from their faces. Some people can easily and accurately identify others’ gender, age, race, or emotional state — even from a glimpse of their faces. However others may lack the ability to detect or interpret them. Case in point, a patent filed in 2014 by Facebook described plans to detect users emotions and deliver specific content, based on those emotions, through computing devices such as laptops, mobile phones and tablets that have a digital camera. Recent progress in AI and computer vision has been largely driven by the widespread adoption of deep neural networks (DNN), or neural networks composed of a large number of hidden layers. DNNs mimic the neocortex by simulating large, multi-level networks of interconnected neurons. DNNs excel at recognizing patterns in large, unstructured data such as digital images, sound, or text, and analyzing such patterns to make predictions. DNNs are increasingly outperforming humans in visual tasks such as image classification, facial recognition, or diagnosing skin cancer. The superior performance of DNNs offers an opportunity to identify links between characteristics and facial features that might be missed or misinterpreted by the human brain. Michal Kosinski, a Stanford University professor, conducted research suggesting that artificial intelligence (AI) can detect the sexual orientation of people based on photos. He mentions that sexual orientation was just one of many characteristics that algorithms would be able to predict through facial recognition. Using photos, AI will be able to identify people’s political views, whether they have high IQs, whether they are predisposed to criminal behavior, whether they have specific personality traits and many other private, personal details that could carry huge social consequences, he said. Faces contain a significant amount of information, and using large datasets of photos, sophisticated computer programs can uncover trends and learn how to distinguish key traits with a high rate of accuracy. With Kosinski’s AI, an algorithm used online dating photos to create a program that could correctly identify sexual orientation 91% of the time with men and 83% with women, just by reviewing a handful of photos. A Feature Able to be Used Against One's Will The iPhone X’s facial recognition capabilities could spell disaster for those wanting to keep their private data from the prying eyes of law enforcement. While the convenience of not having to lift a finger to unlock a phone is being touted as a selling point by Apple, the potential for privacy invasion at the hands of police has people worried. Police require a warrant to unlock and check your phone, but they don’t need one to compel you to use your fingerprint to unlock it. Run through the following scenario: Police demand access to your iPhone X. Cannot compel you without warrant? No problem, they turn phone to face you, unlocks with FaceID. In 2014, a Virginia judge ruled police could force users to unlock their phones using their fingerprints. In February 2016, a judge in Los Angeles signed a search warrant to make a woman unlock her iPhone with her fingerprint. Due to Fifth Amendment protections around self-incrimination in the US, police can’t force a person to give over their passcode, as it’s considered “knowledge.” Albeit, a fingerprint or a face, however, is a different scenario. This is worrying for the vast amount of people who are unlawfully detained and illegally searched. Data Being Used Against the User Beyond the violation of privacy, there are larger implications by which the intelligence agencies are able to hijack individual computers and phones (including iPhones, Blackberries and Androids), take over the device, record its every use, movement, and even the sights and sounds of the room it is in. With the help of this facility, and many others like it, each day the NSA is able to intercept and store 1.7 billion electronic communications. Since it's inception, this secret industry has boomed and is worth billions of dollars per year. There are commercial firms that now sell special software that analyze this data and turn it into powerful tools that can be used by military and intelligence agencies. Around the world, mass surveillance contractors are helping intelligence agencies spy on individuals and ‘communities of interest’ on an industrial scale. The Wikileaks Spy Files reveal the details of which companies are making billions selling sophisticated tracking tools to government buyers, flouting export rules, and turning a blind eye to dictatorial regimes that abuse human rights. Sentient World Simulation
Remarkably, this is precisely what is happening. It is called the “Sentient World Simulation.” The program’s aim, according to its creator, is to be a “continuously running, continually updated mirror model of the real world that can be used to predict and evaluate future events and courses of action.” In practical terms that equates to a computer simulation of the planet complete with billions of “nodes” representing every person on the earth. The project is based out of Purdue University in Indiana at the Synthetic Environment for Analysis and Simulations Laboaratory. It is led by Alok Chaturvedi, who in addition to heading up the Purdue lab also makes the project commercially available via his private company, Simulex, Inc. which boasts an array of government clients, including the Department of Defense and the Department of Justice, as well as private sector clients like Eli Lilly and Lockheed Martin. The program can be used to predict what would happen in the event of a large scale tsunami, for example, or how people would react during a bioterror attack. Businesses can use the models to predict how a new product would fare in the market, what kind of marketing plans would be most effective, or how best to streamline a company’s organization. The original concept paper for the project was published in 2006 and in 2007 it was reported that both Homeland Security and the Defense Department were already using the system to simulate the American public’s reaction to various crises. In the intervening five years, however, there has been almost no coverage at all of the Sentient World Simulation or its progress in achieving a model of the earth. The Sentient World Simulation is one example of one program run by one company for various governmental and Fortune 500 clients. But it is a significant peek behind the curtain at what those who are really running our society want: complete control over every facet of our lives achieved through a complete invasion of everything that was once referred to as “privacy.” Ultimately, it should be noted that all technology can be used as either a tool or as a weapon. But when the technology is in the hands of multinational, monopoly corporations with government influences and coercion, it may be best to side with skepticism and not with open arms. ReferencesCorbett, J. (2012). Sentient World Simulation: Meet Your DoD Clone : The Corbett Report. [online] Corbettreport.com. Available at: https://www.corbettreport.com/sentient-world-simulation-meet-your-dod-clone/ [Accessed 24 Sep. 2017]. Krannert.purdue.edu. (2017). Seas Labs. [online] Available at: http://www.krannert.purdue.edu/centers/perc/html/aboutperc/seaslabs/seaslabs.htm [Accessed 24 Sep. 2017]. Priest, D. and Arkin, W. (2010). A hidden world, growing beyond control (Printer friendly version)| washingtonpost.com. [online] Projects.washingtonpost.com. Available at: http://projects.washingtonpost.com/top-secret-america/articles/a-hidden-world-growing-beyond-control/print/ [Accessed 24 Sep. 2017]. RT International. (2017). iPhone X facial recognition could give cops easy access to your cell. [online] Available at: https://www.rt.com/news/403229-iphone-face-id-police/ [Accessed 24 Sep. 2017]. Wang, Y., & Kosinski, M. (2017). Deep neural networks are more accurate than humans at detecting sexual orientation from facial images. Journal of Personality and Social Psychology Wikileaks.org. (2014). WikiLeaks - The Spy Files. [online] Available at: https://wikileaks.org/the-spyfiles.html [Accessed 15 Sep. 2017].
0 Comments
Leave a Reply. |
This feed contains research, news, information, observations, and ideas at the level of the world.
Archives
May 2024
Categories
All
|
||||||||


 RSS Feed
RSS Feed

