|
2030 UnMasked is a documentary revealing the connection between Covid-19, Vaccines, Masks, the Banking System, and the upcoming “Great Reset”.
This documentary is for anyone realizing something is wrong in the world. Especially for those “just waking up”. It’s uncomfortable to learn that so many things you’ve been told are untrue and this documentary is intended to help make sense of WHY so many things are happening, HOW they are happening, and also WHAT you can do about it. We can’t obey our way out of tyranny. Mass disobedience is the best way to move forward and helping as many people become AWARE is one of the first places to start.
0 Comments
Vandana Shiva is an Indian scholar, environmental activist, physicist, food sovereignty advocate, and anti-globalization author. Based in Delhi, Shiva has written more than 20 books. Shiva founded the Research Foundation for Science, Technology, and Natural Resource Policy (RFSTN), an organization devoted to developing sustainable methods of agriculture, in 1982. She has traveled the world spreading a powerful message of oneness and interconnectedness.
Widespread poverty, social unrest, and economic polarization have become our lived reality as the top 1% of the world’s seven-billion-plus population pushes the planet―and all its people―to the social and ecological brink. Vandana Shiva takes on the billionaire dictators of Gates, Buffet, and Mark Zuckerberg, as well as other modern empires like Big Tech, Big Pharma, and Big Ag, whose blindness to the rights of people, and to the destructive impact of their construct of linear progress, have wrought havoc across the world. Their single-minded pursuit of profit has undemocratically enforced uniformity and monocultures, division and separation, monopolies and external control―over finance, food, energy, information, healthcare, and even relationships. Basing her analysis on explosive facts, Shiva exposes the 1%’s model of philanthrocapitalism, which is about deploying unaccountable money to bypass democratic structures, derail diversity, and impose totalitarian ideas based on One Science, One Agriculture, and One History. Instead, Shiva calls for the resurgence of:
With these core goals, people can reclaim their right to: Live Free. Think Free. Breathe Free. Eat Free. The universe is the internet is the library is the internet is the universe. Or is it? And if so, who are the librarians? And if we have all the information we can ever want, does that mean we have knowledge or wisdom? If not, how do we make it? Or who will make it for us? Join James in this classic "Film, Literature and the New World Order" examination of “The Library of Babel” by Jorge Luis Borges.
Chamath Palihapitiya, Founder, CEO Social Capital and former Facebook executive, warned about the unintended consequences of social media at Stanford Graduate School of Business: "I think we have created tools that are ripping apart the social fabric of how society works. The short-term, dopamine-driven feedback loops we’ve created are destroying how society works. No civil discourse, no cooperation; misinformation, mistruth. You are being programmed"
As the former executive states, we compound the problems in, and curate, our lives around this perceived sense of perfection because we get rewarded in these short-term signals (hearts, likes, thumbs up), and we conflate that with value and truth. Instead, what it really is, is fake, brittle popularity, that is short-term, and it leaves you even more (admit it) vacant and empty. Watch the original, full-length video here During his View From The Top talk, Chamath Palihapitiya, founder and CEO of Social Capital, discussed how money is an instrument of change which should be used to make the world a better place. “Money drives the world for better or for worse. Money is going to be made and allocated – you have a moral imperative to get it and then use it to make a difference.“
Now openly admitted, governments and militaries around the world employ armies of keyboard warriors to spread propaganda and disrupt their online opposition. Their goal? To shape public discourse around global events in a way favorable to their standing military and geopolitical objectives. Their method? The Weaponization of Social Media.
U.S. President Donald Trump on Friday, January 19, 2018 said he signed into law a bill renewing the National Security Agency’s warrantless internet surveillance program. “Just signed 702 Bill to reauthorize foreign intelligence collection,” Trump wrote on Twitter, referring to legislation passed by the U.S. Congress that extends Section 702 of the Foreign Intelligence Surveillance Act (FISA). The law is renewed for six years and with minimal changes the National Security Agency (NSA) program, which gathers information from foreigners overseas and also collects an unknown amount of communications belonging to Americans. Without Trump’s signature, Section 702 had been set to expire on Friday, though intelligence officials had said the surveillance program could continue to operate until April. Under the law, the NSA is allowed to eavesdrop on vast amounts of digital communications from foreigners living outside the United States via U.S. companies like Facebook, Verizon, and Google. But the program also incidentally scoops up Americans’ communications, including when they communicate with a foreign target living overseas, and can search those messages without a warrant. The White House, U.S. intelligence agencies and congressional Republican leaders have said the program is indispensable to national security, vital to protecting U.S. allies and needs little or no revision. Privacy advocates say it allows the NSA and other intelligence agencies to grab data belonging to Americans in a way that represents an affront to the U.S. Constitution. ReferencesVolz, D. (2018). Trump signs bill renewing NSA's internet surveillance program. [online] Reuters. Available at: https://www.reuters.com/article/us-usa-trump-cyber-surveillance/trump-signs-bill-renewing-nsas-internet-surveillance-program-idUSKBN1F82MK?feedType=RSS&feedName=domesticNews [Accessed 23, Jan. 2018].
From Corbettreport.com: When WWII ended and the American deep state welded the national security establishment into place with the National Security Act, the world entered into a new era: the era of the military-industrial complex. But when the Cold War ended and the “Clash of Civilizations” became the new existential threat, the deep state found an opening for another paradigm shift. As the all-pervasive threat of terrorism became the carte blanche for total surveillance, the powers-that-shouldn’t-be found the organizing principal of our age would not be military hardware, but data itself. Welcome to the age of the information-industrial complex. This is The Corbett Report. Of all the things that President Dwight D. Eisenhower did during his years in office, it is for a single phrase from his farewell address that he is best remembered today: “the military-industrial complex.” “In the councils of government, we must guard against the acquisition of unwarranted influence, whether sought or unsought, by the military-industrial complex. The potential for the disastrous rise of misplaced power exists and will persist.” It is not difficult to see why these words passed so quickly into the political lexicon. Think of their explanatory power. Why did the US use inflated estimates of Russian missile capabilities to justify stockpiling a nuclear arsenal that was more than sufficient to destroy the planet several times over? The military-industrial complex. Why did America send 50,000 of its own to fight and die in the jungles of Vietnam, killing untold millions of Vietnamese (not to mention Cambodians)? The military-industrial complex. Why did the US use the public’s fear and anger over 9/11 and a phony panic over non-existent weapons of mass destruction to justify the illegal invasion and trillion dollar occupation of Iraq? The military-industrial complex. Why did Nobel Peace Prize laureate Obama expand the fictitious “war on terror” into Pakistan and Yemen and Somalia, refuse to close Guantanamo despite his earlier promises to the contrary, commit US forces to “kinetic military action” in Libya without so much as seeking Congressional approval, and launch a new era of covert drone warfare? The military-industrial complex. Why has Trump not only continued but further expanded the US military presence in Africa, increased US aid to Israel and Saudi Arabia, actively enabled the war crimes in Yemen that have led to the largest cholera outbreak in human history, and killed more civilians in his first 9 months in office than former drone-king Obama killed in his entire 8 year presidency? The military-industrial complex. When you think about it, it’s rather remarkable that such a phrase was ever uttered by a President of the United States, much less a former five-star general. Could you imagine any modern-day President talking about something like the “military-industrial complex” and its attempted “acquisition of unwarranted influence” without immediately dismissing the idea as a conspiracy theory? Over the decades there has been much speculation about Eisenhower’s use of the phrase, and what precisely he was warning against. Some have argued that the phrase was prompted by Eisenhower’s discovery that the Rand Corporation was grossly misrepresenting the Soviet’s military capabilities to John F. Kennedy, who ended up using the Rand invented (and completely fictitious) “missile gap” threat as a cornerstone of his 1960 presidential election campaign. Whatever the case, it is perhaps time to revisit Eisenhower’s most famous speech. What Eisenhower is ultimately describing is the rise of American fascism; the merger of government and corporate power. What term can better capture the nature of early 21st century American political life? Is there any longer any doubt that the military-industrial complex has reached its ultimate expression in firms like Blackwater (aka “Xe” aka “Academi”) and its military contractor brethren? Is there any other word but ‘fascism’ to describe a state of affairs when a Secretary of Defense can commission a study from a private contractor to examine whether the US military should be using more private contractors, only for that same Secretary of Defense to leave office and become president of the company that conducted the study, only to leave that company to become Vice President of the US and begin waging a war that relies heavily on no-bid contracts awarded to that same company based on the recommendation that it made in its original study? Yet this is precisely the case of Dick Cheney and Halliburton. It would be difficult to think of a more blatant example of the military-industrial complex fascism that Eisenhower was warning of. But as it turns out, there was another warning about fascism embedded in that farewell address that has received far less attention than the ‘military-industrial complex’ formulation, perhaps because there is no catchphrase hook to describe it: “Today, the solitary inventor, tinkering in his shop, has been overshadowed by task forces of scientists in laboratories and testing fields. In the same fashion, the free university, historically the fountainhead of free ideas and scientific discovery, has experienced a revolution in the conduct of research. Partly because of the huge costs involved, a government contract becomes virtually a substitute for intellectual curiosity. For every old blackboard there are now hundreds of new electronic computers.” Given that this warning came in 1961, before the age of communications satellites or personal computers or the internet, it was a remarkably prescient observation. If scientific research half a century ago was dominated by federal grants and expensive computer equipment, how much more true is that for us today, half a century later? So what is the problem with this? As Ike explained: “Yet, in holding scientific research and discovery in respect, as we should, we must also be alert to the equal and opposite danger that public policy could itself become the captive of a scientific-technological elite.” Here again the warning is of fascism. But instead of the military-industrial fascism that dominated so much of the 20th century, he was describing here a new fascistic paradigm that was but barely visible at the time that he gave his address: a scientific-technological one. Once again, the threat is that the industry that grows up around this government-sponsored activity will, just like the military-industrial complex, begin to take over and shape the actions of that same government. In this case, the warning is not one of bombs and bullets but bits and bytes, not tanks and fighter jets but hard drives and routers. Today we know this new fascism by its innocuous sounding title “Big Data,” but in keeping with the spirit of Eisenhower’s remarks, perhaps it would be more fitting to call it the “information-industrial complex.” The concept of an information-industrial complex holds equally explanatory power for our current day and age as the military-industrial complex hypothesis held in Eisenhower’s time. Why is a company like Google going to such lengths to capture, track and database all information on the planet? The information-industrial complex. Why were all major telecom providers and internet service providers mandated by federal law to hardwire in back door access to American intelligence agencies for the purpose of spying on all electronic communications? The information-industrial complex. Why would government after government around the world target encryption as a key threat to their national security, and why would banker after banker call for bitcoin and other cryptocurrencies to be banned even as they plan to set up their own, central bank-administered digital currencies? The information-industrial complex. The effects of this synthesis are more and more felt in our everyday lives. Every single day hundreds of millions of people around the world are interfacing with Microsoft software or Apple hardware or Amazon cloud services running on chips and processors supplied by Intel or other Silicon Valley stalwarts. Google has become so ubiquitous that its very name has become a verb meaning “to search for something on the internet.” The 21st century version of the American dream is encapsulated in the story of Mark Zuckerberg, a typical Harvard whizkid whose atypical rise to the status of multi-billionaire was enabled by a social networking tool by the name of “Facebook” that he developed. But how many people know the flip side of this coin, the one that demonstrates the pervasive government influence in shaping and directing these companies’ rise to success, and the companies’ efforts to aid the government in collecting data on its own citizens? How many know, for instance, that Google has a publicly acknowledged relationship with the NSA? Or that a federal judge has ruled that the public does not have the right to know the details of that relationship? Or that Google Earth was originally the brainchild of Keyhole Inc., a company that was set up by the CIA’s own venture capital firm, In-Q-Tel, using satellite data harvested from government “Keyhole” class reconnaissance satellites? Or that the former CEO of In-Q-Tel, Gilman Louie, sat on the board of the National Venture Capital Association with Jim Breyer, head of Accel Partners, who provided 12 million dollars of seed money for Facebook? Or that in 1999, a back door for NSA access was discovered in Microsoft’s Windows operating system source code? Or that Apple founder Steve Jobs was granted security clearance by the Department of Defense for still-undisclosed reasons while heading Pixar in 1988, as was the former head of AT&T and numerous others in the tech industry? The connections between the IT world and the government’s military and intelligence apparatus run deep. In fact, the development of the IT industry is intimately intertwined with the US Air Force, the Department of Defense and its various branches (including, famously, DARPA), and, of course, the CIA. A cursory glance at the history of the rise of companies like Mitre Corporation, Oracle, and other household electronics and software firms should suffice to expose the extent of these relations, and the existence of what we might dub an “information-industrial complex.” But what does this mean? What are the ramifications of such a relationship? Although the signs have been there for decades, perhaps the most startling example of what lies at the heart of this relationship has been revealed by the whistleblowers at the heart of the National Security Agency, one of the most secretive arms of the American intelligence apparatus. While Edward Snowden has received the most attention with his “revelation” of the PRISM program, much of the information about the NSA’s ability to surveil all electronic communications has been revealed over the past decade by NSA whistleblowers like Russ Tice, William Binney, Thomas Drake and J. Kirk Wiebe, third-party contractors like Snowden and AT&T whistleblower Mark Klein, and independent journalists like James Bamford. Together, the story they tell is of a truly Orwellian society in which all communications are being captured and analyzed by the NSA, and, with the advent of facilities like the new data center in Utah, presumably stored indefinitely for use at any future time in any future investigation for any pretense by anyone with authorization to access that data. According to Snowden, this includes lowly third-party contractors like himself operating at NSA subcontractors like Booz Allen Hamilton in the vast (and expanding) private intelligence industry that has grown up around the information-industrial complex in the exact same way as private military contractors like Blackwater formed around the military-industrial complex. In some ways, this information-industrial complex is even more insidious than its military-industrial counterpart. For all of the ills caused by the military-industrial complex (and there are many), at the very least it required some sort of excuse to drain the American people’s resources, and its failures (like the Vietnam quagmire or the debacle in Iraq) happened in the clear light of day. In the information-industrial complex, where vast spying programs happen in the shadows and under the cover of “national security” it takes whistleblowers and insiders willing to risk it all even to find out what is being done by these shadowy agencies and their private sector contractors. Even worse, the entire Orwellian spy grid is being run on the flimsiest of pretenses (the “war on terror”) that has no defined end point, and “justifies” turning that spy grid inward, on the American people themselves. Surely Eisenhower never envisaged the monstrosity that this information-industrial complex has become, but the foresight he saw in identifying its early stages over half a century ago is remarkable. The problem is that we are even further away from heeding the warning that he delivered in that 1961 address than we were at that time: “It is the task of statesmanship to mold, to balance, and to integrate these and other forces, new and old, within the principles of our democratic system – ever aiming toward the supreme goals of our free society.” If only this was the rhetoric that was shaping today’s debate on the issue, instead of the well-worn canard that we must “strike a balance” between freedom and security. Sadly, until such time that the National Security Act of 1947 is repealed and the cover of national security is lifted from the dark actors that populate this sector, the information-industrial complex is unlikely to be quashed-or even hampered-anytime soon. ReferencesCorbett, J. (2017). Episode 325 – The Information-Industrial Complex : The Corbett Report. [online] Corbettreport.com. Available at: https://www.corbettreport.com/episode-325-the-information-industrial-complex/ [Accessed 18 Dec. 2017].
In accordance with the Privacy Act of 1974, the Department of Homeland Security (DHS) proposes to modify a current DHS system of records titled, “Department of Homeland Security/U.S. Citizenship and Immigration Services, U.S. Immigration and Customs Enforcement, U.S. Customs and Border Protection—001 Alien File, Index, and National File Tracking System of Records.” This system of records contains information regarding transactions involving an individual as he or she passes through the U.S. immigration process. DHS is updating the DHS/USCIS/ICE/CBP-001 Alien File, Index, and National File Tracking System of Records to include the following substantive changes, related to social media:
References Federal Register. (2017). Privacy Act of 1974; System of Records. [online] Available at: https://www.federalregister.gov/documents/2017/09/18/2017-19365/privacy-act-of-1974-system-of-records [Accessed 19 Oct. 2017].
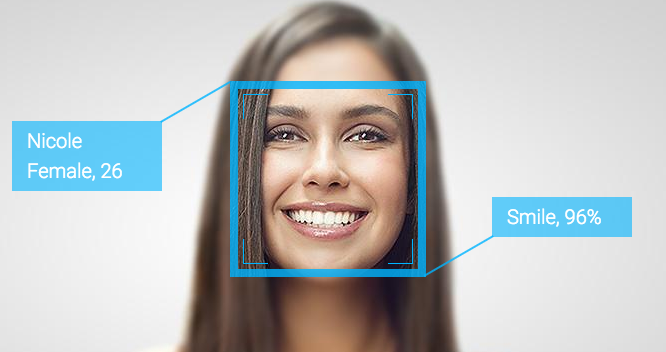
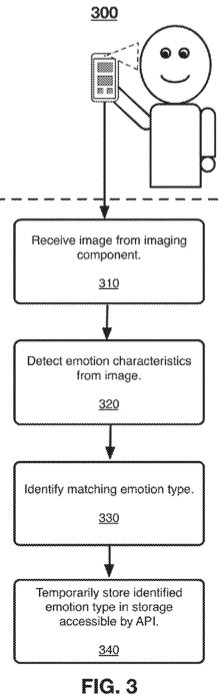
A patent filed in 2014 describes plans to detect users emotions and deliver specific content, based on those emotions, through computing devices such as laptops, mobile phones and tablets that have a digital camera. "A need exists for delivering content a user that may be of current interest to them...[which] may be determined based upon their current emotional state." The patent goes on, "current content delivery systems typically do not utilize passive imaging information. Thus, a need exists for a content delivery solution that takes advantage of available passive imaging data to provide content to a user with improved relevancy." The patent works by an application programming interface (API) component that is able to utilize the imaging component to detect emotion characteristics and store an association between the presented type of emotion and the detected emotion characteristics in the storage component. Once detected and identified, an emotion type may be stored, either temporarily for a defined period of time, or permanently in a user profile. "Content delivery may be performed by an application stored on a device, such as a social networking application, or using a browser application, which may access content from the internet. Content may include, but is not limited to, social networking posts, photos, videos, audio, games, advertisements, or applications made available online or through an application store[d] on a device." "Devices without limitation include a mobile device, a personal digital assistant, a mobile computing device, a smart phone, a cellular telephone, a handset, a one-way pager, a two-way pager, a messaging device, a computer, a personal computer, a desktop computer, a laptop computer, a notebook computer, a handheld computer, a tablet computer, or a wearable computer, such as a smart watch." "Applications may include, but are not limited to, native mobile applications, web applications, desktop applications, or any combination thereof. Examples of native mobile applications may include social networking applications, newsreader applications, photography applications, video applications, media applications, search applications, games, e-reading applications, or the like." "Devices may further include sensors, which may include accelerometer, temperature, gravity, light, accleration, magnetic field, orientation, pressure, rotational vector, or other sensors capable of sensing characteristics of a device and its environment." Examples of operating systems that may be used by device include Apple iOS, Apple OS X, Google Android, Google Chrome OS, Microsoft Windows, or Microsoft Windows Phone.
Keep in mind, this isn't the first time Facebook has explored ways of manipulating its users. In 2014, Facebook ran a social experiment exploiting the emotions of nearly 700,000 users to determine whether negative or positive content would impact their emotions, in which it has been established to be very effective (Kramer, Guillory & Hancock, 2014). Whether this technology will be implemented or not, in the meantime, it may be best to put tape over your devices' cameras, unless you would prefer to participate, and thus consent to, the end of your right to privacy. ReferencesGrasso, S., & Baker-Whitelaw, G. (2017). Facebook patent application describes spying on users through their webcams. The Daily Dot. Retrieved 28 July 2017, from https://www.dailydot.com/debug/facebook-spy-webcam-patent-ads/ Kramer, A., Guillory, J., & Hancock, J. (2014). Experimental evidence of massive-scale emotional contagion through social networks. Proceedings Of The National Academy Of Sciences, 111(24), 8788-8790. http://dx.doi.org/10.1073/pnas.1320040111 TECHNIQUES FOR EMOTION DETECTION AND CONTENT DELIVERY - FACEBOOK, INC.. (2017). Freepatentsonline.com. Retrieved 28 July 2017, from http://www.freepatentsonline.com/y2015/0242679.html |
This feed contains research, news, information, observations, and ideas at the level of the world.
Archives
May 2024
Categories
All
|
 RSS Feed
RSS Feed

