|
In an effort to eradicate weeds and boost yields, Monsanto released their newly developed dicamba-resistant, genetically-engineered seeds. Although a small problem emerged when the volatile herbicide drifted from those applications and began to wipe out the crops of neighboring farmers who didn't plant Monsanto's dicamba-resistant seeds. The EPA has reported that farmers in 25 states submitted more than 2,700 claims to state agricultural agencies that neighbors’ dicamba spraying destroyed 3.6 million acres of soybeans. The herbicide is also blamed for damaging other crops, such as cantaloupe and pumpkins. Now, after allegedly wiping out millions of acres of farmland across the Midwest, Monsanto once again finds itself in a familiar spot: the courtroom. In October, the agricultural giant sued the Arkansas State Plant Board following the board’s decision to restrict Monsanto’s new herbicide and propose tougher restrictions on similar weed killers ahead of the 2018 growing season. Monsanto claims its herbicide is being held to an unfair standard. About 900,000 acres of crops were reported damaged in Arkansas. The massive crop damage prompted Arkansas’s Plant Board to propose the idea of prohibiting dicamba use from mid-April through the end of October to safeguard growing plants. The state has refused to approve Monsanto’s dicamba product for use in Arkansas, saying it needs further analysis by University of Arkansas researchers. Meanwhile, farmers are exploring their own legal options with some joining a class-action lawsuit against Monsanto and BASF, the chemical-based company behind dicamba, seeking compensation for damaged crops. Seems like it may be time for Monsanto executives to start pulling some strings at the EPA again... References Zerohedge.com. (2017). Monsanto In Court Again As Powerful New Herbicide Accidently Kills 3.6 Million Acres Of Crops. [online] Available at: http://www.zerohedge.com/news/2017-11-09/monsanto-court-again-powerful-new-herbicide-accidently-kills-36-million-acres-crops [Accessed 21 Dec. 2017].
0 Comments
TransCanada Corp shut part of its Keystone oil pipeline system after a 5,000-barrel leak in South Dakota, the company said on Thursday, November 16th, four days before neighboring Nebraska was set to decide on the company’s long-delayed Keystone XL pipeline. The amount leaked is equivalent to about 210,000 gallons of oil. This is the largest Keystone oil spill to date in South Dakota, said Brian Walsh, a spokesman for the state's Department of Environment and Natural Resources. There were no initial reports of the oil spill affecting waterways, water systems or wildlife, he said. TransCanada discovered the leak in the town of Amherst at 6 a.m. on Thursday after systems detected a drop in pressure, and worked with authorities as it investigates the cause. U.S. President Donald Trump has made Keystone XL a key plank in his energy policy and handed TransCanada a federal permit in March, reversing former President Barack Obama’s decision to reject the line on environmental grounds after years of study. The Nebraska Public Service Commission, or PSC, was scheduled on Monday, November 20th, to announce and approve the decision on whether the proposed pipeline route through the state is in the best interests of Nebraskans. Native American groups have argued the pipeline would cut across their sovereign lands. Other states have already approved XL’s route. According to TransCanada, the spill in South Dakota led the company to shut the Keystone pipeline from Hardisty, Alberta, to Cushing, Oklahoma, and to Wood River and Patoka in Illinois. Although the southern leg of the system to the Gulf Coast remained operational. References KMBC. (2017). Keystone pipeline leaks 210,000 gallons of oil in South Dakota. [online] Available at: http://www.kmbc.com/article/keystone-pipeline-shuts-down-across-several-states-after-leak-company-says/13788870 [Accessed 21 Dec. 2017].
Reuters. (2017). Keystone oil pipeline leaks in South Dakota, as Nebraska weighs XL. [online] Available at: https://www.reuters.com/article/us-transcanada-keystone-spill/keystone-oil-pipeline-leaks-in-south-dakota-as-nebraska-weighs-xl-idUSKBN1DG30K [Accessed 21 Dec. 2017]. The San Francisco SPCA (a Society for the Prevention of Cruelty to Animals), an animal advocacy and pet adoption group, has deployed an autonomous robot in an effort to patrol local areas for crime and deter homeless people from setting up camps along the sidewalks. The City of San Francisco ordered the SPCA to keep its robot off the sidewalks or face a penalty of up to $1,000 per day for operating in the public right-of-way without a permit.
SPCA rents the robots for $7 an hour — $3 less than a security guard's hourly wage. Knightscope has over 19 clients in five US states. Most customers, including Microsoft, Uber, and Juniper Networks, put the robots to work patrolling parking lots and office buildings. The K9 robot circling the SPCA has drawn mixed responses. Within the first week of the robot's deployment, some people who were setting up a homeless encampment nearby allegedly put a tarp over it, knocked it over, and put barbecue sauce on all the sensors. One wonders what the human backlash will be once a vast portion of America's middle class realizes that it has been made obsolete courtesy of robots who can do its job faster, smarter, much more efficiently and for a fraction of the cost. References Green, A. (2017). Security robot that deterred homeless encampments in the Mission gets rebuke from the city. [online] Bizjournals.com. Available at: https://www.bizjournals.com/sanfrancisco/news/2017/12/08/security-robot-homeless-spca-mission-san-francisco.html [Accessed 19 Dec. 2017].
Robinson, M. (2017). Robots are being used to deter homeless people from setting up camp in San Francisco. [online] Business Insider. Available at: http://www.businessinsider.com/security-robots-are-monitoring-the-homeless-in-san-francisco-2017-12 [Accessed 19 Dec. 2017]. From Corbettreport.com: When WWII ended and the American deep state welded the national security establishment into place with the National Security Act, the world entered into a new era: the era of the military-industrial complex. But when the Cold War ended and the “Clash of Civilizations” became the new existential threat, the deep state found an opening for another paradigm shift. As the all-pervasive threat of terrorism became the carte blanche for total surveillance, the powers-that-shouldn’t-be found the organizing principal of our age would not be military hardware, but data itself. Welcome to the age of the information-industrial complex. This is The Corbett Report. Of all the things that President Dwight D. Eisenhower did during his years in office, it is for a single phrase from his farewell address that he is best remembered today: “the military-industrial complex.” “In the councils of government, we must guard against the acquisition of unwarranted influence, whether sought or unsought, by the military-industrial complex. The potential for the disastrous rise of misplaced power exists and will persist.” It is not difficult to see why these words passed so quickly into the political lexicon. Think of their explanatory power. Why did the US use inflated estimates of Russian missile capabilities to justify stockpiling a nuclear arsenal that was more than sufficient to destroy the planet several times over? The military-industrial complex. Why did America send 50,000 of its own to fight and die in the jungles of Vietnam, killing untold millions of Vietnamese (not to mention Cambodians)? The military-industrial complex. Why did the US use the public’s fear and anger over 9/11 and a phony panic over non-existent weapons of mass destruction to justify the illegal invasion and trillion dollar occupation of Iraq? The military-industrial complex. Why did Nobel Peace Prize laureate Obama expand the fictitious “war on terror” into Pakistan and Yemen and Somalia, refuse to close Guantanamo despite his earlier promises to the contrary, commit US forces to “kinetic military action” in Libya without so much as seeking Congressional approval, and launch a new era of covert drone warfare? The military-industrial complex. Why has Trump not only continued but further expanded the US military presence in Africa, increased US aid to Israel and Saudi Arabia, actively enabled the war crimes in Yemen that have led to the largest cholera outbreak in human history, and killed more civilians in his first 9 months in office than former drone-king Obama killed in his entire 8 year presidency? The military-industrial complex. When you think about it, it’s rather remarkable that such a phrase was ever uttered by a President of the United States, much less a former five-star general. Could you imagine any modern-day President talking about something like the “military-industrial complex” and its attempted “acquisition of unwarranted influence” without immediately dismissing the idea as a conspiracy theory? Over the decades there has been much speculation about Eisenhower’s use of the phrase, and what precisely he was warning against. Some have argued that the phrase was prompted by Eisenhower’s discovery that the Rand Corporation was grossly misrepresenting the Soviet’s military capabilities to John F. Kennedy, who ended up using the Rand invented (and completely fictitious) “missile gap” threat as a cornerstone of his 1960 presidential election campaign. Whatever the case, it is perhaps time to revisit Eisenhower’s most famous speech. What Eisenhower is ultimately describing is the rise of American fascism; the merger of government and corporate power. What term can better capture the nature of early 21st century American political life? Is there any longer any doubt that the military-industrial complex has reached its ultimate expression in firms like Blackwater (aka “Xe” aka “Academi”) and its military contractor brethren? Is there any other word but ‘fascism’ to describe a state of affairs when a Secretary of Defense can commission a study from a private contractor to examine whether the US military should be using more private contractors, only for that same Secretary of Defense to leave office and become president of the company that conducted the study, only to leave that company to become Vice President of the US and begin waging a war that relies heavily on no-bid contracts awarded to that same company based on the recommendation that it made in its original study? Yet this is precisely the case of Dick Cheney and Halliburton. It would be difficult to think of a more blatant example of the military-industrial complex fascism that Eisenhower was warning of. But as it turns out, there was another warning about fascism embedded in that farewell address that has received far less attention than the ‘military-industrial complex’ formulation, perhaps because there is no catchphrase hook to describe it: “Today, the solitary inventor, tinkering in his shop, has been overshadowed by task forces of scientists in laboratories and testing fields. In the same fashion, the free university, historically the fountainhead of free ideas and scientific discovery, has experienced a revolution in the conduct of research. Partly because of the huge costs involved, a government contract becomes virtually a substitute for intellectual curiosity. For every old blackboard there are now hundreds of new electronic computers.” Given that this warning came in 1961, before the age of communications satellites or personal computers or the internet, it was a remarkably prescient observation. If scientific research half a century ago was dominated by federal grants and expensive computer equipment, how much more true is that for us today, half a century later? So what is the problem with this? As Ike explained: “Yet, in holding scientific research and discovery in respect, as we should, we must also be alert to the equal and opposite danger that public policy could itself become the captive of a scientific-technological elite.” Here again the warning is of fascism. But instead of the military-industrial fascism that dominated so much of the 20th century, he was describing here a new fascistic paradigm that was but barely visible at the time that he gave his address: a scientific-technological one. Once again, the threat is that the industry that grows up around this government-sponsored activity will, just like the military-industrial complex, begin to take over and shape the actions of that same government. In this case, the warning is not one of bombs and bullets but bits and bytes, not tanks and fighter jets but hard drives and routers. Today we know this new fascism by its innocuous sounding title “Big Data,” but in keeping with the spirit of Eisenhower’s remarks, perhaps it would be more fitting to call it the “information-industrial complex.” The concept of an information-industrial complex holds equally explanatory power for our current day and age as the military-industrial complex hypothesis held in Eisenhower’s time. Why is a company like Google going to such lengths to capture, track and database all information on the planet? The information-industrial complex. Why were all major telecom providers and internet service providers mandated by federal law to hardwire in back door access to American intelligence agencies for the purpose of spying on all electronic communications? The information-industrial complex. Why would government after government around the world target encryption as a key threat to their national security, and why would banker after banker call for bitcoin and other cryptocurrencies to be banned even as they plan to set up their own, central bank-administered digital currencies? The information-industrial complex. The effects of this synthesis are more and more felt in our everyday lives. Every single day hundreds of millions of people around the world are interfacing with Microsoft software or Apple hardware or Amazon cloud services running on chips and processors supplied by Intel or other Silicon Valley stalwarts. Google has become so ubiquitous that its very name has become a verb meaning “to search for something on the internet.” The 21st century version of the American dream is encapsulated in the story of Mark Zuckerberg, a typical Harvard whizkid whose atypical rise to the status of multi-billionaire was enabled by a social networking tool by the name of “Facebook” that he developed. But how many people know the flip side of this coin, the one that demonstrates the pervasive government influence in shaping and directing these companies’ rise to success, and the companies’ efforts to aid the government in collecting data on its own citizens? How many know, for instance, that Google has a publicly acknowledged relationship with the NSA? Or that a federal judge has ruled that the public does not have the right to know the details of that relationship? Or that Google Earth was originally the brainchild of Keyhole Inc., a company that was set up by the CIA’s own venture capital firm, In-Q-Tel, using satellite data harvested from government “Keyhole” class reconnaissance satellites? Or that the former CEO of In-Q-Tel, Gilman Louie, sat on the board of the National Venture Capital Association with Jim Breyer, head of Accel Partners, who provided 12 million dollars of seed money for Facebook? Or that in 1999, a back door for NSA access was discovered in Microsoft’s Windows operating system source code? Or that Apple founder Steve Jobs was granted security clearance by the Department of Defense for still-undisclosed reasons while heading Pixar in 1988, as was the former head of AT&T and numerous others in the tech industry? The connections between the IT world and the government’s military and intelligence apparatus run deep. In fact, the development of the IT industry is intimately intertwined with the US Air Force, the Department of Defense and its various branches (including, famously, DARPA), and, of course, the CIA. A cursory glance at the history of the rise of companies like Mitre Corporation, Oracle, and other household electronics and software firms should suffice to expose the extent of these relations, and the existence of what we might dub an “information-industrial complex.” But what does this mean? What are the ramifications of such a relationship? Although the signs have been there for decades, perhaps the most startling example of what lies at the heart of this relationship has been revealed by the whistleblowers at the heart of the National Security Agency, one of the most secretive arms of the American intelligence apparatus. While Edward Snowden has received the most attention with his “revelation” of the PRISM program, much of the information about the NSA’s ability to surveil all electronic communications has been revealed over the past decade by NSA whistleblowers like Russ Tice, William Binney, Thomas Drake and J. Kirk Wiebe, third-party contractors like Snowden and AT&T whistleblower Mark Klein, and independent journalists like James Bamford. Together, the story they tell is of a truly Orwellian society in which all communications are being captured and analyzed by the NSA, and, with the advent of facilities like the new data center in Utah, presumably stored indefinitely for use at any future time in any future investigation for any pretense by anyone with authorization to access that data. According to Snowden, this includes lowly third-party contractors like himself operating at NSA subcontractors like Booz Allen Hamilton in the vast (and expanding) private intelligence industry that has grown up around the information-industrial complex in the exact same way as private military contractors like Blackwater formed around the military-industrial complex. In some ways, this information-industrial complex is even more insidious than its military-industrial counterpart. For all of the ills caused by the military-industrial complex (and there are many), at the very least it required some sort of excuse to drain the American people’s resources, and its failures (like the Vietnam quagmire or the debacle in Iraq) happened in the clear light of day. In the information-industrial complex, where vast spying programs happen in the shadows and under the cover of “national security” it takes whistleblowers and insiders willing to risk it all even to find out what is being done by these shadowy agencies and their private sector contractors. Even worse, the entire Orwellian spy grid is being run on the flimsiest of pretenses (the “war on terror”) that has no defined end point, and “justifies” turning that spy grid inward, on the American people themselves. Surely Eisenhower never envisaged the monstrosity that this information-industrial complex has become, but the foresight he saw in identifying its early stages over half a century ago is remarkable. The problem is that we are even further away from heeding the warning that he delivered in that 1961 address than we were at that time: “It is the task of statesmanship to mold, to balance, and to integrate these and other forces, new and old, within the principles of our democratic system – ever aiming toward the supreme goals of our free society.” If only this was the rhetoric that was shaping today’s debate on the issue, instead of the well-worn canard that we must “strike a balance” between freedom and security. Sadly, until such time that the National Security Act of 1947 is repealed and the cover of national security is lifted from the dark actors that populate this sector, the information-industrial complex is unlikely to be quashed-or even hampered-anytime soon. ReferencesCorbett, J. (2017). Episode 325 – The Information-Industrial Complex : The Corbett Report. [online] Corbettreport.com. Available at: https://www.corbettreport.com/episode-325-the-information-industrial-complex/ [Accessed 18 Dec. 2017].
A Duluth-based health system - a company founded in 2003 that owns and operates 15 hospitals and 75 medical clinics located in Minnesota, Wisconsin, North Dakota and Idaho - has fired about 50 employees who refused to get an annual flu shot (KWG, 2017). A few days later it was reported that a total of Essentia Health 69 employees had been let go (Dyer, 2017). Essentia Health announced last month that employees would be required to get vaccinated for influenza to help keep patients from getting infected, or else receive a religious or medical exemption. Minnesota employees were particularly disturbed by the requirement, as state law does not mandate influenza vaccinations for health care workers. Vaccine Mandate Based on Flawed and Weak Evidence Researchers have sought out for the scientific evidence used to push mandatory flu vaccinations of all hospital personnel. There are four cluster randomized controlled trials, conducted exclusively in long-term care facilities and nursing homes that have specifically assessed indirect patient benefits from health care worker influenza vaccination which have been most often cited in the support of mandatory health care worker policies. Two pivotal systematic reviews and meta-analyses have been published summarizing and pooling these four cRCT findings, but reached different conclusions about the strength of that evidence. Given this, researchers analyzed the four randomized controlled trials underpinning policies of enforced health-care worker influenza vaccination and discovered implausibly large reductions in patient risk to health-care worker vaccination, casting serious doubts on their validity. In other words, the impression that unvaccinated heath-care workers place their patients at great influenza peril is greatly exaggerated. Instead, the risk attributable to health-care workers remains unknown and the number needed to vaccinate to achieve patient benefit still requires better understanding (De Serres et al., 2017). References De Serres, G., Skowronski, D., Ward, B., Gardam, M., Lemieux, C., Yassi, A., Patrick, D., Krajden, M., Loeb, M., Collignon, P. and Carrat, F. (2017). Influenza Vaccination of Healthcare Workers: Critical Analysis of the Evidence for Patient Benefit Underpinning Policies of Enforcement. PLOS ONE, 12(1), p.e0163586. https://doi.org/10.1371/journal.pone.0163586
Dyer, O. (2017). US healthcare company fires 69 employees for refusing flu vaccination. BMJ, p.j5473. https://doi.org/10.1136/bmj.j5473 KGW. (2017). Company fires about 50 workers for refusing to get flu shot. [online] Available at: http://www.kgw.com/news/company-fires-about-50-workers-for-refusing-to-get-flu-shot/493776350 [Accessed 16 Dec. 2017]. Mercola, J. (2017). Vaccine Deficient Employees Fired to Gain Health Care Funding. [online] Mercola.com. Available at: https://articles.mercola.com/sites/articles/archive/2017/12/05/mandatory-influenza-vaccinations.aspx [Accessed 16 Dec. 2017]. The Transportation Security Administration (TSA) plans to move forward with progressively implementing facial recognition and other biometric data into screenings at various airports across the United States. The agency began testing out the methods, which also include iris scans and fingerprints, on volunteers in their PreCheck program at airports over the summer. On November 1, the TSA announced plans to expand the program. The TSA Pre-Application program claims to enhance “aviation security by permitting TSA to better focus its limited security resources on passengers who are more likely to pose a threat to civil aviation, while also facilitating and improving the commercial aviation travel experience for the public.” Under the program, individuals are to submit biographic information (including, but not limited to, name, date of birth, gender, prior and current addresses, contact information, country of birth, images of identity documents, proof of citizenship/immigration status) and biometric data (such as fingerprints, iris scans, or facial images) to a TSA contractor, which forwards the information to the agency. From Pilot Program to National Policy In June and July of 2017, the TSA “launched a proof of concept initiative at Hartsfield-Jackson Atlanta International Airport and Denver International Airport to determine whether fingerprints from TSA Pre✓® Application Program applicants,” who volunteered to participate, could be used for identity verification. The TSA is currently “seeking a revision to the currently approved request to allow for the collection of additional biometrics, particularly facial images but may include other biometrics such as iris, from TSA Pre✓® Application Program applicants.” The TSA claims that "the regular collection of biometrics, such as facial images, will provide TSA with the ability to use those biometrics for identity verification at TSA checkpoints, potentially eliminating the need to show identity documents and improving both security and the customer experience.” Some privacy advocates disagree with the attempted expansion. According to the Electronic Frontier Foundation, the TSA’s push to expand its use of biometrics is part of a broader push by the Department of Homeland Security (DHS) to nationalize the collection and use of biometric data. According to an assessment by the DHS, in 2016 the U.S. Customs and Border Protection (CBP) will operate a test at Hartsfield-Jackson Atlanta International Airport, in Atlanta, Georgia in order to identify reliable and cost-effective border management capabilities (such as verifying biometrics of departing travelers) that can be deployed nationwide and across multiple modes of travel. Photos of travelers taken during boarding will be compared against photos taken previously (U.S. passport, U.S. visa, and other DHS encounters) and stored in existing CBP systems. Prior to the departure of each flight, CBP will collect facial images and boarding pass information of all travelers, including U.S. citizens, as they pass through the passenger loading bridge to board their flight. CBP will use this data to test the ability of CBP data systems to confirm a traveler’s identity using a facial biometric comparison as the traveler departs from the United States. Initially, the DHS states that the data will be stored for no longer than one year after the test. Since then the DHS updated it's stance, stating "CBP retains biographic exit records for 15 years for U.S. citizens and lawful permanent residents and 75 years for non-immigrant aliens." These actions would be carried out without congressional authorization. Initially these practices were to be limited to international flights. However, according to John Wagner, deputy assistant commissioner at CBP, the TSA is now seeking to expand the collection of biometric data to domestic flights, as well. DHS Data in the Hands of Third Parties Concerns should also be raised regarding the storage of biometric data in the hands of third parties, including but not limited to airlines. DHS sub-agencies are sharing data with the FBI, and the TSA Pre-check program shares it with private companies it uses as contractors. Americans should be concerned about these proposals because the data collected—your fingerprint, the image of your face, and the scan of your iris—will be stored in the databases of the FBI, DHS, and other non-government third parties (such as commerical airlines and air authorities), which will be searched for immigration, law enforcement, and intelligence checks, including checks against latent prints associated with unsolved crimes. This vast data collection will create a huge security risk. As seen with the 2017 Equifax breach, no government agency or private company is capable of fully protecting your private and sensitive information. While losing your social security or credit card information may result in fraud, those numbers can easily be changed. On the other hand, if your biometrics get into the wrong hands, you can’t change your face. ReferencesDhs.gov. (2016). Departure Information Systems Test. [online] Available at: https://www.dhs.gov/sites/default/files/publications/privacy-pia-cbp-dis%20test-june2016.pdf [Accessed 15 Dec. 2017].
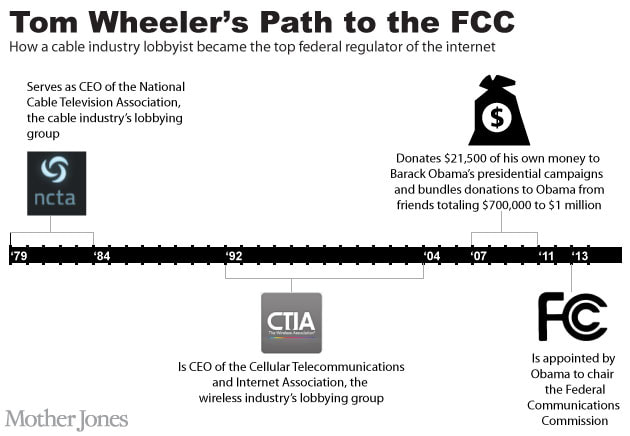
Dhs.gov. (2017). Traveler Verification Service (TVS). [online] Available at: https://www.dhs.gov/sites/default/files/publications/privacy-pia-cbp030-tvs-september2017.pdf [Accessed 15 Dec. 2017]. Lynch, J. (2017). TSA Plans to Use Face Recognition to Track Americans Through Airports. [online] Electronic Frontier Foundation. Available at: https://www.eff.org/deeplinks/2017/11/tsa-plans-use-face-recognition-track-americans-through-airports [Accessed 15 Dec. 2017]. Regulations.gov. (2017). Agency Information Collection Activities; Proposals, Submissions, and Approvals: TSA Pre-Check Application Program. [online] Available at: https://www.regulations.gov/document?D=TSA-2014-0001-0021 [Accessed 15 Dec. 2017]. Wedler, C. (2017). TSA Plans to Use Facial Recognition to Track Americans in US Airports. [online] The Anti-Media. Available at: http://theantimedia.org/tsa-facial-recognition-biometrics/ [Accessed 15 Dec. 2017]. The Federal Communications Commission (FCC) chairman, Ajit Pai, announced plans to dismantle net neutrality November 21, 2017. Pai said it best, "Under my proposal, the federal government will stop micromanaging the Internet. Instead, the FCC would simply require Internet service providers to be transparent about their practices so that consumers can buy the service plan that’s best for them and entrepreneurs and other small businesses can have the technical information they need to innovate." Net Neutrality: the principle that Internet service providers must treat all data on the Internet the same, and not discriminate or charge differently by user, content, website, platform, application, type of attached equipment, or method of communication. Net neutrality refers to a network, the Internet, in which all data is regulated, or treated equally. Under the principle of net neutrality, Internet services providers (ISPs) are unable to intentionally block, slow down or charge money for specific websites and online content. This means, for instance, that your ISP can't form a special deal with a big company like Netflix or Amazon to let their data pass through the network more quickly or downgrade other sites to an Internet "slow lane" where data passes to users more slowly. At first glance, net neutrality is good for the average Internet user. But there is much more to net neutrality than that, and it starts with Tom Wheeler. Tom Wheeler: The Cable Industry Lobbyist and Top Federal Regulator of the Internet Tom Wheeler, former FCC Chairman, former President of the National Cable and Telecommunications & Internet Association, and former CEO of the Cellular Telecommunications and Internet Association. Wheeler is a lobbyist for the very industry he is supposedly regulating. Now, net neutrality wasn't Wheeler's idea, but was rather proposed under the Obama Administration. The official regulatory plan was published in a 400 page document. The FCC reclassified ISPs as common carriers under Title II of the Federal Communications Act of 1934, as well as Title III of the same Act and Section 706 of the Telecommunications Act of 1996. Now the FCC has the authority to regulate ISPs, even at the rates at which they charge their customers. In Plain English In other words, under net neutrality (more specifically Title II), the Internet is classified by the U.S. government as a public utility. This is a blank check for government control across the board. This means that local, state, and federal fees that apply specifically to the Title II services will create billions of dollars in new charges that will be pushed on to American Internet users. It means that any branch of FCC commissioners will be able to wield powers to enforce the rules over any service on the Internet in any way they see fit. Essentially, the future of the Internet lies in the hands of the FCC under net neutrality. The FCC called it a triumph of “free expression and democratic principles.” It was anything but. It was actually a power grab, creating an Internet communication cartel not unlike the way the banking system works under the Federal Reserve. Goodbye Net Neutrality; Hello Competition Net neutrality closed down market competition by putting government and its corporate backers in charge of deciding who can and cannot play in the market. It erected hurdles for smaller companies to jump over while hugely subsidizing the largest content providers. In effect, with net neutrality, no price reductions in internet service would be seen. Your bills may go up and there would be very little competition. In other words, it was like all government regulation: most of the costs were unseen, and the benefits were concentrated in the hands of the ruling class. Think of the medical industry, which is now entirely owned by a non-competitive cartel of industry insiders. This would be the future of the internet under net neutrality. Goodbye net neutrality! No more government-managed control of the industry. No more price fixing. No more of the largest players using government power to protect their monopoly structure. The end of net neutrality is the best single deregulatory initiative yet taken by the Trump administration. We should take our deregulation where we can get it. ReferencesCorbett, J. (2015). Net “Neutrality,” or, How To Regulate the Internet to Thunderous Applause : The Corbett Report. [online] Corbettreport.com. Available at: https://www.corbettreport.com/net-neutrality-or-how-to-regulate-the-internet-to-thunderous-applause/ [Accessed 7 Dec. 2017].
Tucker, J. (2017). Goodbye Net Neutrality; Hello Competition. [online] Fee.org. Available at: https://fee.org/articles/goodbye-net-neutrality-hello-competition/ [Accessed 7 Dec. 2017]. |
This feed contains research, news, information, observations, and ideas at the level of the world.
Archives
May 2024
Categories
All
|

 RSS Feed
RSS Feed

