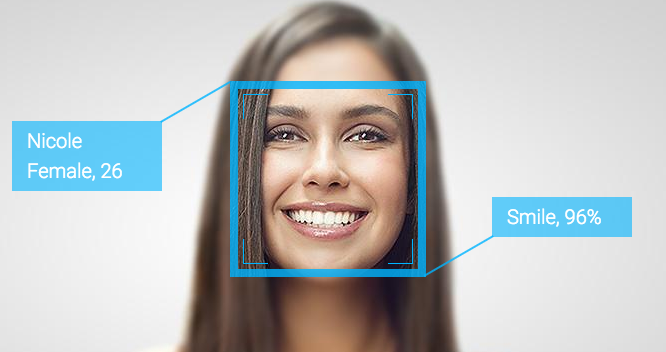
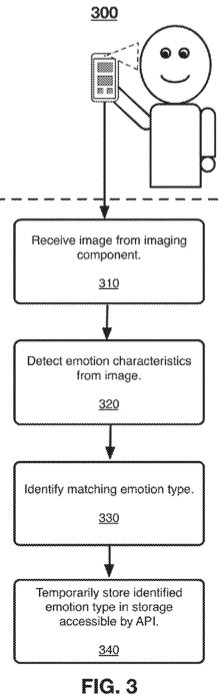
A patent filed in 2014 describes plans to detect users emotions and deliver specific content, based on those emotions, through computing devices such as laptops, mobile phones and tablets that have a digital camera. "A need exists for delivering content a user that may be of current interest to them...[which] may be determined based upon their current emotional state." The patent goes on, "current content delivery systems typically do not utilize passive imaging information. Thus, a need exists for a content delivery solution that takes advantage of available passive imaging data to provide content to a user with improved relevancy." The patent works by an application programming interface (API) component that is able to utilize the imaging component to detect emotion characteristics and store an association between the presented type of emotion and the detected emotion characteristics in the storage component. Once detected and identified, an emotion type may be stored, either temporarily for a defined period of time, or permanently in a user profile. "Content delivery may be performed by an application stored on a device, such as a social networking application, or using a browser application, which may access content from the internet. Content may include, but is not limited to, social networking posts, photos, videos, audio, games, advertisements, or applications made available online or through an application store[d] on a device." "Devices without limitation include a mobile device, a personal digital assistant, a mobile computing device, a smart phone, a cellular telephone, a handset, a one-way pager, a two-way pager, a messaging device, a computer, a personal computer, a desktop computer, a laptop computer, a notebook computer, a handheld computer, a tablet computer, or a wearable computer, such as a smart watch." "Applications may include, but are not limited to, native mobile applications, web applications, desktop applications, or any combination thereof. Examples of native mobile applications may include social networking applications, newsreader applications, photography applications, video applications, media applications, search applications, games, e-reading applications, or the like." "Devices may further include sensors, which may include accelerometer, temperature, gravity, light, accleration, magnetic field, orientation, pressure, rotational vector, or other sensors capable of sensing characteristics of a device and its environment." Examples of operating systems that may be used by device include Apple iOS, Apple OS X, Google Android, Google Chrome OS, Microsoft Windows, or Microsoft Windows Phone.
Keep in mind, this isn't the first time Facebook has explored ways of manipulating its users. In 2014, Facebook ran a social experiment exploiting the emotions of nearly 700,000 users to determine whether negative or positive content would impact their emotions, in which it has been established to be very effective (Kramer, Guillory & Hancock, 2014). Whether this technology will be implemented or not, in the meantime, it may be best to put tape over your devices' cameras, unless you would prefer to participate, and thus consent to, the end of your right to privacy. ReferencesGrasso, S., & Baker-Whitelaw, G. (2017). Facebook patent application describes spying on users through their webcams. The Daily Dot. Retrieved 28 July 2017, from https://www.dailydot.com/debug/facebook-spy-webcam-patent-ads/ Kramer, A., Guillory, J., & Hancock, J. (2014). Experimental evidence of massive-scale emotional contagion through social networks. Proceedings Of The National Academy Of Sciences, 111(24), 8788-8790. http://dx.doi.org/10.1073/pnas.1320040111 TECHNIQUES FOR EMOTION DETECTION AND CONTENT DELIVERY - FACEBOOK, INC.. (2017). Freepatentsonline.com. Retrieved 28 July 2017, from http://www.freepatentsonline.com/y2015/0242679.html
0 Comments
Three Square Market, a Wisconsin-based company, announced that is it about to become the first in the U.S. to offer microchip implants to their employees, at the cost of the company. Each RFID chip (Radio-Frequency Identification) is about the size of a single grain of rice, which will be implanted between a person's thumb and forefinger. Each microchip will cost roughly $300 and will allow the employees to enter the building, purchase items in the break room, login to their computers, and use the copy machine. But those certainly are not the limits of the chip. “Eventually, this technology will become standardized allowing you to use this as your passport, public transit, all purchasing opportunities, etc,” Three Square Market CEO, Todd Westby, said. Westby added the RFID data is both encrypted and secure and that, "there's no GPS tracking at all."
Three Square Market designs software for break room markets that are commonly found in office complexes. According to Westby, the end goal of this move is to allow people to purchase items using a microchip implanted inside a person's hand, similar to using a smart phone. "We'll come up, scan the item," he explained, while showing how the process will work at an actual break room market kiosk. "We'll hit pay with a credit card, and it's asking to swipe my proximity payment now. I'll hold my hand up, just like my cell phone, and it'll pay for my product." A Worldwide Phenomena One Swedish rail company, SJ, has been offering passengers the option of using a biometric chip implanted into their hand in lieu of a paper train ticket. The tiny chip has the same technology as Oyster cards and contactless bank cards – NFC (Near Field Communication) – to enable conductors to scan passengers’ hands. The convenience is only applicable to those who already have the biometric implant, as SJ is not offering to chip people. Around 2,000 Swedes have had the surgical implant to date, most of them employed in the tech industry. State-owned operator SJ has said it expects about 200 people to take up the microchip method, but users must be signed up as a loyalty program member to access the service. Customers buy tickets in the normal way by logging onto the website or mobile app, and their membership number, which is the reference code for the ticket, is linked to their chip. While this technology is relatively old, there are still kinks to be ironed out with the system. Some passengers’ LinkedIn profiles were appearing instead of their train tickets when conductors scanned their biometric chip, while a number of train crew haven’t got the new SJ app which facilitates the scanning of biometric chips yet. Reactions to the idea have been largely positive they said, although some security issues have been raised. “Of course there’s mixed reactions. Some people are concerned with the privacy issue and that’s something we take really seriously. We came up with using the membership number which doesn’t tell anyone anything – a third party couldn’t make anything of it even if they got hold of it", says SJ’s spokesperson. “Some people are confused and think they can be tracked via microchip – but if that’s something they’re worried about, they should be more concerned by their mobile phone and credit card use. You can already be tracked in many different ways other than a microchip.” Although anonymity is a serious struggle in modern society, collectively we should choose privacy over convenience when it comes to adopting "advancements" like these. By voluntarily participating in these programs, you consent to your data being collected and analyzed, justifying the process for other people to join. Let us keep in mind that this technology is very old, as new biometric identification systems are being utilized worldwide. What could go wrong? ReferencesCoffey, H. (2017). This Swedish rail company is letting commuters pay using microchips in their hands. The Independent. Retrieved 28 July 2017, from http://www.independent.co.uk/travel/news-and-advice/sj-rail-train-tickets-hand-implant-microchip-biometric-sweden-a7793641.html
Rosenthal, J. (2017). Wisconsin Company to Implant Microchips in Employees. KSTP. Retrieved 26 July 2017, from http://kstp.com/news/wisconsin-company-to-implant-microchips-in-employees-three-square-market/4549459/#.WXVQVSc74iY.twitter The global war on terror has entered the digital age and it’s no longer a question of if there will be an attack on the world wide web but when! In this video Dan Dicks of Press For Truth speaks with James Corbett of The Corbett Report about what a possible cyber attack scenario might look like, who the perpetrators are likely to be, who the scapegoat will be to take the fall and most importantly what we all can do about it BEFORE it happens.
transcript from The International Forecaster: 5. The "Visual Microphone" As we all know, what we call "sound" is essentially a wave propagating through a medium like air, displacing particles and causing oscillations in the pressure and velocity of those particles. These oscillations are detected by our ears and converted into nerve impulses that our brain interprets as sound. So what if you can't directly perceive that wave itself, but the effect of that wave on another subject? Could you reconstruct that sound just from seeing the effect of the sound wave? Well, let's not keep anybody in suspense here. The answer is yes. Yes, you can. As a team of researchers from Microsoft, Adobe and MIT demonstrated in 2014, it is possible to examine video of everyday objects in environments where a sound is playing for the minute, almost imperceptible vibrations that the sound causes on the object's surface. These vibrations can then be "reconstructed" and a recognizable version of that sound can be reproduced from the video alone...without any audio being recorded. The technology itself is truly incredible. Check out the video if you haven't yet done so to see what these researchers were able to accomplish. They reconstruct "Mary Had A Little Lamb" from the vibrations on the leafs of a house plant in the room where the song was being played using nothing other than a high speed camera. They reconstruct a voice recording of a man reciting "Mary Had A Little Lamb" from the vibrations on a bag of chips using a high speed camera filming the chips through a soundproof window. Most impressive of all, they even reconstruct a recognizable version of the song from a ketchup packet taken with nothing but an ordinary, consumer version 60 fps DSLR camera. This is a truly remarkable technology and goes to show just how incredible the products of human ingenuity really are...and just how advanced the spying capabilities of the intelligence agencies already are. If you think MIT researchers are working on technology like this without the full knowledge of the alphabet soupers, you're not living in the real world. Even Cracked.com, a humor website that derides "conspiracy theories" every chance it gets, knows precisely what this tech will be (is already being?) used for: "The researchers say they can do the same thing with a piece of foil or even a potted plant, which has far-reaching implications in the field of, well, spying on people. And probably other things." But mostly spying. 4. X-ray Backscatter Vans Remember those ridiculous "X-ray specs" they used to sell in the back of comic books? The ones that were guaranteed to help you see through solid objects? Somehow even at the age of 8 you knew they were a bunch of baloney (even if you still joked with your friends about how you would use them). Well you can stop worrying about it: they were baloney and you were right not to buy them. But you might be happy to hear that the technology to actually see through objects does exist now...until you hear it was developed for the Department of Homeland Security. It's been almost a decade since the DHS revealed the prototype of the LEXID, a handheld x-ray imaging device that allows agents to see through walls. (Surely you remember me covering that in Episode 025 of my podcast, right?) At the time the full working devices were slated to be a year away from being ready to deploy on the street into the hot little hands of the upstanding men and women of the Department of Fatherland Security. But four years later we instead got roving backscatter x-ray scanner vans. That was when American Science & Engineering (the company in Massachusetts, not the concept) announced they had already sold 500 of their Z Backscatter Vans (or "ZBVs") to "U.S. and foreign government agencies." The vans are designed to rove around the streets blasting everything in sight with X-rays in order to (we are told) discover contraband and dangerous cargo in vehicles and other hiding places. Sound dangerous? It sure is. But are we really expecting the DHS to care whether or not they're sending random innocent people to an early grave when there's billions in federal funding for such technologies to burn through and cool spying tech like this to play with? Of course not. 3. Stingrays Back in November 2014 the story broke that the increasingly inaccurately named Department of "Justice" was sending up a fleet of Cessnas with devices that could mimic cellphone towers in order to collect communication data on criminal suspects. The devices (dubbed "Stingrays" by people who apparently think the scheme isn't already Bond villain cartoonish enough) spoof cellphones into giving up their identity and location data, and allowed the DOJ to scoop up the cell phone conversations and text messages of thousands of people per flight, all supposedly justified because they were looking for a handful of bad guys' data. Sound like a clear violation of Fourth Amendment rights? It certainly is, but that didn't even cause the FBI to blink. Once the program was exposed they simply declared: "Warrants? We don't need no stinking warrants!" (or the legalese equivalent thereof) and continued on their merry cellphone spoofing way. To the surprise of absolutely no one, it came out a couple of months later that the Stingrays were not merely being deployed by the top elite law enforcement professionals of the FBI but local law enforcement, too, and that the Bureau had tried with all its might to keep that knowledge from ever seeing the light of day. So yes, it is quite possible that your cellphone call is being scooped up by a fake cellphone tower and stored in the vaults of some bureau or agency, somewhere or other. And if all of that doesn't sound quite Orwellian enough...don't worry! The latest revelations from a leak last December show that the Stingray is just one of a catalogue of items that the police state can (and does) use to spy on your cell phone. Perhaps unsurprisingly, it seems that local law enforcement have been increasingly dipping into the military-industrial tech treasure chest for their spying needs, a phenomenon prompted by the problem-reaction-solution set up of events like the San Bernardino shooting. These technologies allow for precise tracking and geolocation of a targeted cellphone in more ways than can even be elaborated here. 2. TEMPEST But don't let all this fool you into thinking that the spymasters need physical access to you or your location at all in order to see/hear what you're doing. We're sadly well past that point, as described by Jacob Applebaum in a speech at the annual Chaos Communication Congress in 2013. Now Applebaum himself is a character who probably deserves his own investigation but the bag of NSA goodies that he revealed at 30c3 is nonetheless informative. His presentation, entitled "To Protect and Infect," broke down a series of exploits, backdoors, and good old-fashioned skullduggery that the NSA uses to scoop information out of computers and devices around the world, from secret hardware implants in USB connections to provide wireless backdoors into target networks (dubbed "COTTONMOUTH") to the no-less-imaginatively entitled HOWLERMONKEY. That's a radiofrequency transmitter that the NSA can surreptitiously implant directly into your computer when it is in transit through the mail. But by far the most intriguing part of the presentation came near the end when he revealed this nugget: "Well, what if I told you that the NSA had a specialized technology for beaming energy into you and to the computer systems around you, would you believe that that was real or would that be paranoid speculation of a crazy person?... That exists, by the way." The idea here, apparently, is that by using a continuous wave radar unit, the agents of evil can beam up to 1 kilowatt energy directly into you, effectively lighting up you (and any electronic equipment you're in contact with) like a Christmas tree so that active radar can exfiltrate your data. According to Der Spiegel, “Most of this equipment involves a combination of hardware implants which emit a very inconspicuous signal, and a radio unit aimed, from outside, at the space being monitored. Reflected radar waves are changed by the signal emitted by the implant hidden in the targeted space.” According to the documents published by Der Spiegel, the technology can capture the location of a specific object in the room, words spoken in the room, and even what is displayed on a monitor in the room, all without the need of any active listening device in the room. Even disregarding how utterly insane that sounds, is it safe? Won't that kind of RF energy being beamed directly into people cause cancer? Who knows? Who cares! The eyes in the sky could care less as long as they get their target data. OK, this is all incredibly creepy. But what if you've already typed out your super secret love letter and the NSA wasn't able to intercept it in real time? What if they weren't able to spoof it out of your phone or irradiate you so you glowed like a candle for their radars to scoop up every word? What if it's already a done deal? A fait accomplis? Surely they can't get the info, then, right? What are they going to do, scoop it right out of your brain? 1. Brain Scanners Essentially, yes. They are going to scoop the info out of your brain. As the International Business Times puts it: "Scientists have created a mind-reading machine that allows them to reconstruct images in a person's mind using brain scans." Sound sensational? Well it's not as far off the mark as such hyperbole might sound at first glance. In 2014 researchers at New York University and the University of California showed 300 pictures of faces to six test subjects who were undergoing fMRI scans in order to build up a database of how their brains reacted to facial data. They then showed them pictures of new faces and used the resulting fMRI data to reconstruct crude (but recognizable) versions of those faces. In other words, they "read their mind" and were able to pictorially represent what the subjects were looking at. The technology is still a long way off from being "mind reading devices" in the Buck Rogers sense, but it's a significant step on the way. And this is only the technology that is publicly known about. Are we really to believe that this is truly the cutting edge of such technology and that they don't have something more cutting edge in the skunkworks of DARPA? Scared yet? Well don't be. That's just what they want. Nothing to fear but fear itself "OK, OK, we get it, James!" you're saying right now. "They can see everything, read everything, hear everything. There's no escape. We might as well just give up." Absolutely not. It is important to understand and be knowledgeable about the types of technology that the police state has at its disposal. But let's keep in mind that the only perfect prison is the one that we create in our own minds. The one that stops us from acting out of fear that the jailers will see us. We should always keep in mind that stories about what the intelligence agencies have up their sleeve is always exaggerated and over-played. Their most effective tool is to merely convince you that they see and hear everything. But more often than not, they're flat out lying... ReferencesDavis, A., Rubinstein, M., Wadhwa, N., Mysore, G., Durand, F., & Freeman, W. (2014). The Visual Microphone: Passive Recovery of Sound from Video. Retrieved from https://people.csail.mit.edu/mrub/papers/VisualMic_SIGGRAPH2014.pdf
Kravets, D. (2017). FBI says search warrants not needed to use “stingrays” in public places. Ars Technica. Retrieved 9 July 2017, from https://arstechnica.com/tech-policy/2015/01/fbi-says-search-warrants-not-needed-to-use-stringrays-in-public-places/ Lee, H., & Kuhl, B. (2016). Reconstructing Perceived and Retrieved Faces from Activity Patterns in Lateral Parietal Cortex. Journal Of Neuroscience, 36(22), 6069-6082. http://dx.doi.org/10.1523/jneurosci.4286-15.2016 Stingray Tracking Devices: Who's Got Them?. (2017). American Civil Liberties Union. Retrieved 9 July 2017, from https://www.aclu.org/map/stingray-tracking-devices-whos-got-them ZBV® - American Science & Engineering. (2017). As-e.com. Retrieved 9 July 2017, from http://as-e.com/products-solutions/cargo-vehicle-inspection/mobile/product/zbv/ |
This feed contains research, news, information, observations, and ideas at the level of the world.
Archives
May 2024
Categories
All
|

 RSS Feed
RSS Feed

