|
In a recent interview, Mike Benz, Executive Director of the Foundation for Freedom Online and former Deputy Assistant Secretary at the U.S. Department of State, discussed the evolving landscape of free speech on the Internet and its intersection with geopolitics. According to Benz, free speech on the Internet has been a strategic tool in the realm of statecraft since the early days of its privatization.
Benz highlighted Google's origin as a DARPA grant and its transformation into a military contractor, emphasizing the military-industrial roots of prominent tech companies. He pointed to a paradigm shift in warfare following the annexation of Crimea, leading NATO to acknowledge the importance of controlling the media and social media ecosystem for electoral influence—a concept known as the Gerasimov doctrine. Notably, NATO identified the manipulation of media and social media as a significant threat, with the primary concern being the potential impact on domestic elections across Europe. The interview included a quote from a four-star general, questioning the fate of the U.S. military when major news outlets are reduced to the scale of social media pages. Benz expressed concern about the rise of the censorship industry, describing it as a fundamental inversion of democracy. He argued that the current state of affairs resembles a form of military rule, where controlling narratives and information flow takes precedence. In his view, the essence of democracy has been distorted, with power shifting towards aligning non-governmental organizations, financial entities like BlackRock, major media outlets, and community activist groups. The interview sheds light on the intricate relationship between free speech, technology, and geopolitical dynamics, raising important questions about the impact of information control on democracy and the evolving nature of warfare in the digital age. The national security state is the main driver of censorship and election interference in the United States. "What I’m describing is military rule," says Mike Benz. "It’s the inversion of democracy." transcript
0 Comments
U.S. President Donald Trump on Friday, January 19, 2018 said he signed into law a bill renewing the National Security Agency’s warrantless internet surveillance program. “Just signed 702 Bill to reauthorize foreign intelligence collection,” Trump wrote on Twitter, referring to legislation passed by the U.S. Congress that extends Section 702 of the Foreign Intelligence Surveillance Act (FISA). The law is renewed for six years and with minimal changes the National Security Agency (NSA) program, which gathers information from foreigners overseas and also collects an unknown amount of communications belonging to Americans. Without Trump’s signature, Section 702 had been set to expire on Friday, though intelligence officials had said the surveillance program could continue to operate until April. Under the law, the NSA is allowed to eavesdrop on vast amounts of digital communications from foreigners living outside the United States via U.S. companies like Facebook, Verizon, and Google. But the program also incidentally scoops up Americans’ communications, including when they communicate with a foreign target living overseas, and can search those messages without a warrant. The White House, U.S. intelligence agencies and congressional Republican leaders have said the program is indispensable to national security, vital to protecting U.S. allies and needs little or no revision. Privacy advocates say it allows the NSA and other intelligence agencies to grab data belonging to Americans in a way that represents an affront to the U.S. Constitution. ReferencesVolz, D. (2018). Trump signs bill renewing NSA's internet surveillance program. [online] Reuters. Available at: https://www.reuters.com/article/us-usa-trump-cyber-surveillance/trump-signs-bill-renewing-nsas-internet-surveillance-program-idUSKBN1F82MK?feedType=RSS&feedName=domesticNews [Accessed 23, Jan. 2018].
The Transportation Security Administration (TSA) plans to move forward with progressively implementing facial recognition and other biometric data into screenings at various airports across the United States. The agency began testing out the methods, which also include iris scans and fingerprints, on volunteers in their PreCheck program at airports over the summer. On November 1, the TSA announced plans to expand the program. The TSA Pre-Application program claims to enhance “aviation security by permitting TSA to better focus its limited security resources on passengers who are more likely to pose a threat to civil aviation, while also facilitating and improving the commercial aviation travel experience for the public.” Under the program, individuals are to submit biographic information (including, but not limited to, name, date of birth, gender, prior and current addresses, contact information, country of birth, images of identity documents, proof of citizenship/immigration status) and biometric data (such as fingerprints, iris scans, or facial images) to a TSA contractor, which forwards the information to the agency. From Pilot Program to National Policy In June and July of 2017, the TSA “launched a proof of concept initiative at Hartsfield-Jackson Atlanta International Airport and Denver International Airport to determine whether fingerprints from TSA Pre✓® Application Program applicants,” who volunteered to participate, could be used for identity verification. The TSA is currently “seeking a revision to the currently approved request to allow for the collection of additional biometrics, particularly facial images but may include other biometrics such as iris, from TSA Pre✓® Application Program applicants.” The TSA claims that "the regular collection of biometrics, such as facial images, will provide TSA with the ability to use those biometrics for identity verification at TSA checkpoints, potentially eliminating the need to show identity documents and improving both security and the customer experience.” Some privacy advocates disagree with the attempted expansion. According to the Electronic Frontier Foundation, the TSA’s push to expand its use of biometrics is part of a broader push by the Department of Homeland Security (DHS) to nationalize the collection and use of biometric data. According to an assessment by the DHS, in 2016 the U.S. Customs and Border Protection (CBP) will operate a test at Hartsfield-Jackson Atlanta International Airport, in Atlanta, Georgia in order to identify reliable and cost-effective border management capabilities (such as verifying biometrics of departing travelers) that can be deployed nationwide and across multiple modes of travel. Photos of travelers taken during boarding will be compared against photos taken previously (U.S. passport, U.S. visa, and other DHS encounters) and stored in existing CBP systems. Prior to the departure of each flight, CBP will collect facial images and boarding pass information of all travelers, including U.S. citizens, as they pass through the passenger loading bridge to board their flight. CBP will use this data to test the ability of CBP data systems to confirm a traveler’s identity using a facial biometric comparison as the traveler departs from the United States. Initially, the DHS states that the data will be stored for no longer than one year after the test. Since then the DHS updated it's stance, stating "CBP retains biographic exit records for 15 years for U.S. citizens and lawful permanent residents and 75 years for non-immigrant aliens." These actions would be carried out without congressional authorization. Initially these practices were to be limited to international flights. However, according to John Wagner, deputy assistant commissioner at CBP, the TSA is now seeking to expand the collection of biometric data to domestic flights, as well. DHS Data in the Hands of Third Parties Concerns should also be raised regarding the storage of biometric data in the hands of third parties, including but not limited to airlines. DHS sub-agencies are sharing data with the FBI, and the TSA Pre-check program shares it with private companies it uses as contractors. Americans should be concerned about these proposals because the data collected—your fingerprint, the image of your face, and the scan of your iris—will be stored in the databases of the FBI, DHS, and other non-government third parties (such as commerical airlines and air authorities), which will be searched for immigration, law enforcement, and intelligence checks, including checks against latent prints associated with unsolved crimes. This vast data collection will create a huge security risk. As seen with the 2017 Equifax breach, no government agency or private company is capable of fully protecting your private and sensitive information. While losing your social security or credit card information may result in fraud, those numbers can easily be changed. On the other hand, if your biometrics get into the wrong hands, you can’t change your face. ReferencesDhs.gov. (2016). Departure Information Systems Test. [online] Available at: https://www.dhs.gov/sites/default/files/publications/privacy-pia-cbp-dis%20test-june2016.pdf [Accessed 15 Dec. 2017].
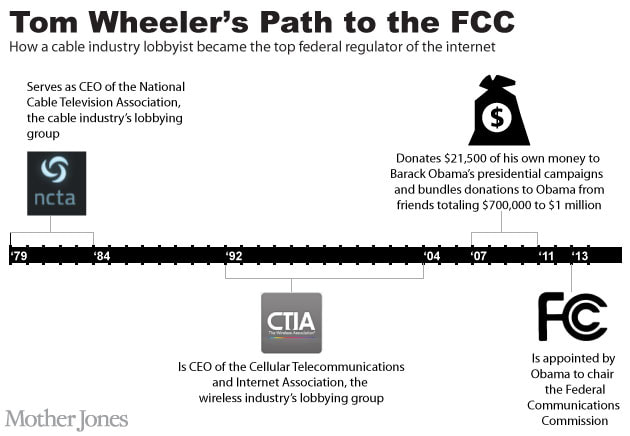
Dhs.gov. (2017). Traveler Verification Service (TVS). [online] Available at: https://www.dhs.gov/sites/default/files/publications/privacy-pia-cbp030-tvs-september2017.pdf [Accessed 15 Dec. 2017]. Lynch, J. (2017). TSA Plans to Use Face Recognition to Track Americans Through Airports. [online] Electronic Frontier Foundation. Available at: https://www.eff.org/deeplinks/2017/11/tsa-plans-use-face-recognition-track-americans-through-airports [Accessed 15 Dec. 2017]. Regulations.gov. (2017). Agency Information Collection Activities; Proposals, Submissions, and Approvals: TSA Pre-Check Application Program. [online] Available at: https://www.regulations.gov/document?D=TSA-2014-0001-0021 [Accessed 15 Dec. 2017]. Wedler, C. (2017). TSA Plans to Use Facial Recognition to Track Americans in US Airports. [online] The Anti-Media. Available at: http://theantimedia.org/tsa-facial-recognition-biometrics/ [Accessed 15 Dec. 2017]. The Federal Communications Commission (FCC) chairman, Ajit Pai, announced plans to dismantle net neutrality November 21, 2017. Pai said it best, "Under my proposal, the federal government will stop micromanaging the Internet. Instead, the FCC would simply require Internet service providers to be transparent about their practices so that consumers can buy the service plan that’s best for them and entrepreneurs and other small businesses can have the technical information they need to innovate." Net Neutrality: the principle that Internet service providers must treat all data on the Internet the same, and not discriminate or charge differently by user, content, website, platform, application, type of attached equipment, or method of communication. Net neutrality refers to a network, the Internet, in which all data is regulated, or treated equally. Under the principle of net neutrality, Internet services providers (ISPs) are unable to intentionally block, slow down or charge money for specific websites and online content. This means, for instance, that your ISP can't form a special deal with a big company like Netflix or Amazon to let their data pass through the network more quickly or downgrade other sites to an Internet "slow lane" where data passes to users more slowly. At first glance, net neutrality is good for the average Internet user. But there is much more to net neutrality than that, and it starts with Tom Wheeler. Tom Wheeler: The Cable Industry Lobbyist and Top Federal Regulator of the Internet Tom Wheeler, former FCC Chairman, former President of the National Cable and Telecommunications & Internet Association, and former CEO of the Cellular Telecommunications and Internet Association. Wheeler is a lobbyist for the very industry he is supposedly regulating. Now, net neutrality wasn't Wheeler's idea, but was rather proposed under the Obama Administration. The official regulatory plan was published in a 400 page document. The FCC reclassified ISPs as common carriers under Title II of the Federal Communications Act of 1934, as well as Title III of the same Act and Section 706 of the Telecommunications Act of 1996. Now the FCC has the authority to regulate ISPs, even at the rates at which they charge their customers. In Plain English In other words, under net neutrality (more specifically Title II), the Internet is classified by the U.S. government as a public utility. This is a blank check for government control across the board. This means that local, state, and federal fees that apply specifically to the Title II services will create billions of dollars in new charges that will be pushed on to American Internet users. It means that any branch of FCC commissioners will be able to wield powers to enforce the rules over any service on the Internet in any way they see fit. Essentially, the future of the Internet lies in the hands of the FCC under net neutrality. The FCC called it a triumph of “free expression and democratic principles.” It was anything but. It was actually a power grab, creating an Internet communication cartel not unlike the way the banking system works under the Federal Reserve. Goodbye Net Neutrality; Hello Competition Net neutrality closed down market competition by putting government and its corporate backers in charge of deciding who can and cannot play in the market. It erected hurdles for smaller companies to jump over while hugely subsidizing the largest content providers. In effect, with net neutrality, no price reductions in internet service would be seen. Your bills may go up and there would be very little competition. In other words, it was like all government regulation: most of the costs were unseen, and the benefits were concentrated in the hands of the ruling class. Think of the medical industry, which is now entirely owned by a non-competitive cartel of industry insiders. This would be the future of the internet under net neutrality. Goodbye net neutrality! No more government-managed control of the industry. No more price fixing. No more of the largest players using government power to protect their monopoly structure. The end of net neutrality is the best single deregulatory initiative yet taken by the Trump administration. We should take our deregulation where we can get it. ReferencesCorbett, J. (2015). Net “Neutrality,” or, How To Regulate the Internet to Thunderous Applause : The Corbett Report. [online] Corbettreport.com. Available at: https://www.corbettreport.com/net-neutrality-or-how-to-regulate-the-internet-to-thunderous-applause/ [Accessed 7 Dec. 2017].
Tucker, J. (2017). Goodbye Net Neutrality; Hello Competition. [online] Fee.org. Available at: https://fee.org/articles/goodbye-net-neutrality-hello-competition/ [Accessed 7 Dec. 2017]. The launch of the so-called AWS Secret Region comes six years after AWS introduced GovCloud, its first data-center region for public-sector customers. AWS has since announced plans to expand GovCloud. The new Secret Region signals interest in using AWS from specific parts of the U.S. government. In 2013, AWS and the CIA signed a $600 million contract to keep up with big data analytics. That event singlehandedly helped Amazon in its effort to sign up large companies to use its cloud, whose core services have been available since 2006. Today AWS counts companies such as Comcast, Hess, Intuit and Lionsgate as customers. AWS' competitors include Microsoft, Google, IBM and Oracle. "With the launch of this new Secret Region, AWS becomes the first and only commercial cloud provider to offer regions to serve government workloads across the full range of data classifications, including Unclassified, Sensitive, Secret, and Top Secret," Amazon said in a blog post. The new region is available to customers as a result of AWS' contract with the intelligence community's Commercial Cloud Services, or C2S, group, and it will meet certain government standards, Amazon said. But the region will also be accessible for U.S. government organizations that aren't part of the intelligence community so long as they have their own "contract vehicles" and sufficient secret-level network access, Amazon said. ReferencesAmazon Web Services. (2017). Announcing the New AWS Secret Region | Amazon Web Services. [online] Available at: https://aws.amazon.com/blogs/publicsector/announcing-the-new-aws-secret-region/ [Accessed 22 Nov. 2017].
Konkel, F. (2017). Sources: Amazon and CIA ink cloud deal -- FCW. [online] FCW. Available at: https://fcw.com/articles/2013/03/18/amazon-cia-cloud.aspx [Accessed 22 Nov. 2017]. Novet, J. (2017). Amazon launches a cloud service for US intelligence agencies. [online] CNBC. Available at: https://www.cnbc.com/2017/11/20/amazon-launches-aws-secret-region.html?__source=twitter%7Cmain [Accessed 22 Nov. 2017]. In accordance with the Privacy Act of 1974, the Department of Homeland Security (DHS) proposes to modify a current DHS system of records titled, “Department of Homeland Security/U.S. Citizenship and Immigration Services, U.S. Immigration and Customs Enforcement, U.S. Customs and Border Protection—001 Alien File, Index, and National File Tracking System of Records.” This system of records contains information regarding transactions involving an individual as he or she passes through the U.S. immigration process. DHS is updating the DHS/USCIS/ICE/CBP-001 Alien File, Index, and National File Tracking System of Records to include the following substantive changes, related to social media:
References Federal Register. (2017). Privacy Act of 1974; System of Records. [online] Available at: https://www.federalregister.gov/documents/2017/09/18/2017-19365/privacy-act-of-1974-system-of-records [Accessed 19 Oct. 2017].
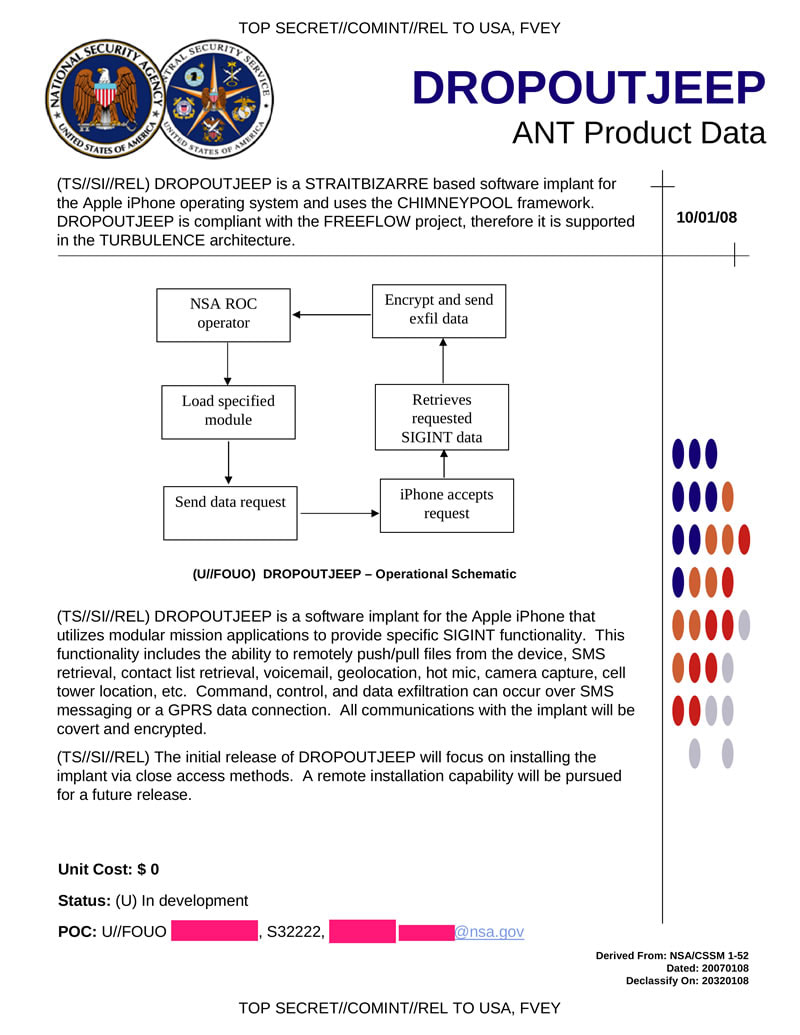
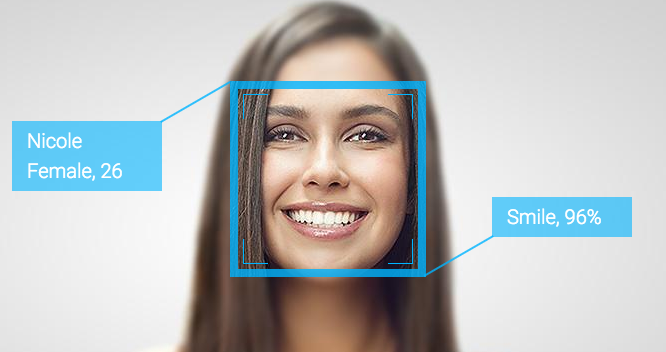
If you haven't already been informed, the new iPhone X was announced September 12, 2017. While the $1,000 device represents a whole new era of technological achievement, many of the new capabilities should raise some concern. Most notable is Face ID; the ability to unlock the device with the user's face and eyes. This feat is accomplished by a number of new sensors built into the front-facing screen, including a dot projector, infrared camera, flood illuminator and proximity sensor. By projecting a field of over 30,000 invisible dots out into the environment, together these sensors are able to constantly scan for and map the geometry of the user's face to unlock the device from multiple angles, even in the dark. In other words, your face is your password. The technology is able model faces and adapt to the changing landscape and aspects of a person’s face as they grow and change. Apple states that the biometric data is stored locally on the device and claims that Face ID cannot be fooled by photographs of faces. Beyond the obvious question, "why is this necessary?", delving deeper into the device and it's data ties with the intelligence agencies, should raise skepticism regarding the true intentions behind the technology. Privacy Violation: Governments Spying Via iPhones According to hundreds of leaked documents via Wikileaks, as many as 160 intelligence contractors in the mass surveillance industry may have access to the data on a single cellular device. Intelligence agencies, military forces and police authorities are able to silently, and on mass, and secretly intercept calls and take over computers without the help or knowledge of the telecommunication providers - no matter the country. Users’ physical location can be tracked if they are carrying a mobile phone, even if it is only on stand by. In addition, systems to infect every Facebook user, or smart-phone owner of an entire population group are and have been on the intelligence market since the rise of the patriot act, due to events that took place on September 11, 2001. Companies like Phoenexia in the Czech Republic collaborate with the military to create speech analysis tools. These speech analysis tools are able to identify individuals by gender, age and stress levels and track them based on ‘voiceprints’. DROPOUTJEEP, a spyware said to be one of the tools employed by the NSA's ANT (Advanced or Access Network Technology) division, is able to gain backdoor access to various electronic devices. DROPOUTJEEP can infiltrate virtually all areas of the iPhone (not only the iPhone X), including voice mail, contact lists, instant messages, and cell tower location. The general response among people who have justified and have been normalized to privacy violation after reading this is, "I have nothing to hide." Why is it that one closes the door when they use the restroom? Or why does one have a password on their phone is the first place? Akin to freedom of speech, privacy is, or should be, a basic human right. But the reality is that the right to privacy no longer exists. By waiving your freedom of privacy and saying, "I have nothing to hide", is equivalent to waiving your freedom of speech and saying, "I have nothing to say." Normalizing Facial Scanning Have you had your fingerprints taken for government ID? Your irises scanned? Your earlobes measured? A microchip implanted? Are you prepared to? Where will you draw the line? Acknowledged or not, this technology is normalizing facial scanning. Let us not be naive, this is a coordinated plan to institute a worldwide biometric id system to track every human on the planet. Faces Contain a Significant Amount of Data The science of judging one’s character from their facial characteristics, or physiognomy, dates back to ancient China and Greece. Aristotle and Pythagoras were among its disciples, and the latter used to select his students based on their facial features. Cesare Lombroso, the founder of criminal anthropology, believed that criminals could be identified by their facial features. There is a growing body of evidence suggesting that character can influence one’s facial appearance, and vice versa. The appearance of an individual's face drives first impressions of others, influencing our expectations and behavior toward them, which, in turn, shapes their character. The existence of such links between facial appearance and character is supported by the fact that people can accurately judge others’ character, psychological states, and demographic traits from their faces. Some people can easily and accurately identify others’ gender, age, race, or emotional state — even from a glimpse of their faces. However others may lack the ability to detect or interpret them. Case in point, a patent filed in 2014 by Facebook described plans to detect users emotions and deliver specific content, based on those emotions, through computing devices such as laptops, mobile phones and tablets that have a digital camera. Recent progress in AI and computer vision has been largely driven by the widespread adoption of deep neural networks (DNN), or neural networks composed of a large number of hidden layers. DNNs mimic the neocortex by simulating large, multi-level networks of interconnected neurons. DNNs excel at recognizing patterns in large, unstructured data such as digital images, sound, or text, and analyzing such patterns to make predictions. DNNs are increasingly outperforming humans in visual tasks such as image classification, facial recognition, or diagnosing skin cancer. The superior performance of DNNs offers an opportunity to identify links between characteristics and facial features that might be missed or misinterpreted by the human brain. Michal Kosinski, a Stanford University professor, conducted research suggesting that artificial intelligence (AI) can detect the sexual orientation of people based on photos. He mentions that sexual orientation was just one of many characteristics that algorithms would be able to predict through facial recognition. Using photos, AI will be able to identify people’s political views, whether they have high IQs, whether they are predisposed to criminal behavior, whether they have specific personality traits and many other private, personal details that could carry huge social consequences, he said. Faces contain a significant amount of information, and using large datasets of photos, sophisticated computer programs can uncover trends and learn how to distinguish key traits with a high rate of accuracy. With Kosinski’s AI, an algorithm used online dating photos to create a program that could correctly identify sexual orientation 91% of the time with men and 83% with women, just by reviewing a handful of photos. A Feature Able to be Used Against One's Will The iPhone X’s facial recognition capabilities could spell disaster for those wanting to keep their private data from the prying eyes of law enforcement. While the convenience of not having to lift a finger to unlock a phone is being touted as a selling point by Apple, the potential for privacy invasion at the hands of police has people worried. Police require a warrant to unlock and check your phone, but they don’t need one to compel you to use your fingerprint to unlock it. Run through the following scenario: Police demand access to your iPhone X. Cannot compel you without warrant? No problem, they turn phone to face you, unlocks with FaceID. In 2014, a Virginia judge ruled police could force users to unlock their phones using their fingerprints. In February 2016, a judge in Los Angeles signed a search warrant to make a woman unlock her iPhone with her fingerprint. Due to Fifth Amendment protections around self-incrimination in the US, police can’t force a person to give over their passcode, as it’s considered “knowledge.” Albeit, a fingerprint or a face, however, is a different scenario. This is worrying for the vast amount of people who are unlawfully detained and illegally searched. Data Being Used Against the User Beyond the violation of privacy, there are larger implications by which the intelligence agencies are able to hijack individual computers and phones (including iPhones, Blackberries and Androids), take over the device, record its every use, movement, and even the sights and sounds of the room it is in. With the help of this facility, and many others like it, each day the NSA is able to intercept and store 1.7 billion electronic communications. Since it's inception, this secret industry has boomed and is worth billions of dollars per year. There are commercial firms that now sell special software that analyze this data and turn it into powerful tools that can be used by military and intelligence agencies. Around the world, mass surveillance contractors are helping intelligence agencies spy on individuals and ‘communities of interest’ on an industrial scale. The Wikileaks Spy Files reveal the details of which companies are making billions selling sophisticated tracking tools to government buyers, flouting export rules, and turning a blind eye to dictatorial regimes that abuse human rights. Sentient World Simulation
Remarkably, this is precisely what is happening. It is called the “Sentient World Simulation.” The program’s aim, according to its creator, is to be a “continuously running, continually updated mirror model of the real world that can be used to predict and evaluate future events and courses of action.” In practical terms that equates to a computer simulation of the planet complete with billions of “nodes” representing every person on the earth. The project is based out of Purdue University in Indiana at the Synthetic Environment for Analysis and Simulations Laboaratory. It is led by Alok Chaturvedi, who in addition to heading up the Purdue lab also makes the project commercially available via his private company, Simulex, Inc. which boasts an array of government clients, including the Department of Defense and the Department of Justice, as well as private sector clients like Eli Lilly and Lockheed Martin. The program can be used to predict what would happen in the event of a large scale tsunami, for example, or how people would react during a bioterror attack. Businesses can use the models to predict how a new product would fare in the market, what kind of marketing plans would be most effective, or how best to streamline a company’s organization. The original concept paper for the project was published in 2006 and in 2007 it was reported that both Homeland Security and the Defense Department were already using the system to simulate the American public’s reaction to various crises. In the intervening five years, however, there has been almost no coverage at all of the Sentient World Simulation or its progress in achieving a model of the earth. The Sentient World Simulation is one example of one program run by one company for various governmental and Fortune 500 clients. But it is a significant peek behind the curtain at what those who are really running our society want: complete control over every facet of our lives achieved through a complete invasion of everything that was once referred to as “privacy.” Ultimately, it should be noted that all technology can be used as either a tool or as a weapon. But when the technology is in the hands of multinational, monopoly corporations with government influences and coercion, it may be best to side with skepticism and not with open arms. ReferencesCorbett, J. (2012). Sentient World Simulation: Meet Your DoD Clone : The Corbett Report. [online] Corbettreport.com. Available at: https://www.corbettreport.com/sentient-world-simulation-meet-your-dod-clone/ [Accessed 24 Sep. 2017]. Krannert.purdue.edu. (2017). Seas Labs. [online] Available at: http://www.krannert.purdue.edu/centers/perc/html/aboutperc/seaslabs/seaslabs.htm [Accessed 24 Sep. 2017]. Priest, D. and Arkin, W. (2010). A hidden world, growing beyond control (Printer friendly version)| washingtonpost.com. [online] Projects.washingtonpost.com. Available at: http://projects.washingtonpost.com/top-secret-america/articles/a-hidden-world-growing-beyond-control/print/ [Accessed 24 Sep. 2017]. RT International. (2017). iPhone X facial recognition could give cops easy access to your cell. [online] Available at: https://www.rt.com/news/403229-iphone-face-id-police/ [Accessed 24 Sep. 2017]. Wang, Y., & Kosinski, M. (2017). Deep neural networks are more accurate than humans at detecting sexual orientation from facial images. Journal of Personality and Social Psychology Wikileaks.org. (2014). WikiLeaks - The Spy Files. [online] Available at: https://wikileaks.org/the-spyfiles.html [Accessed 15 Sep. 2017].
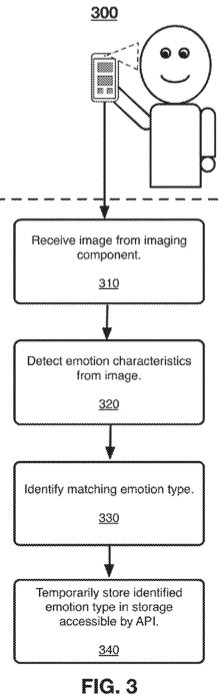
A patent filed in 2014 describes plans to detect users emotions and deliver specific content, based on those emotions, through computing devices such as laptops, mobile phones and tablets that have a digital camera. "A need exists for delivering content a user that may be of current interest to them...[which] may be determined based upon their current emotional state." The patent goes on, "current content delivery systems typically do not utilize passive imaging information. Thus, a need exists for a content delivery solution that takes advantage of available passive imaging data to provide content to a user with improved relevancy." The patent works by an application programming interface (API) component that is able to utilize the imaging component to detect emotion characteristics and store an association between the presented type of emotion and the detected emotion characteristics in the storage component. Once detected and identified, an emotion type may be stored, either temporarily for a defined period of time, or permanently in a user profile. "Content delivery may be performed by an application stored on a device, such as a social networking application, or using a browser application, which may access content from the internet. Content may include, but is not limited to, social networking posts, photos, videos, audio, games, advertisements, or applications made available online or through an application store[d] on a device." "Devices without limitation include a mobile device, a personal digital assistant, a mobile computing device, a smart phone, a cellular telephone, a handset, a one-way pager, a two-way pager, a messaging device, a computer, a personal computer, a desktop computer, a laptop computer, a notebook computer, a handheld computer, a tablet computer, or a wearable computer, such as a smart watch." "Applications may include, but are not limited to, native mobile applications, web applications, desktop applications, or any combination thereof. Examples of native mobile applications may include social networking applications, newsreader applications, photography applications, video applications, media applications, search applications, games, e-reading applications, or the like." "Devices may further include sensors, which may include accelerometer, temperature, gravity, light, accleration, magnetic field, orientation, pressure, rotational vector, or other sensors capable of sensing characteristics of a device and its environment." Examples of operating systems that may be used by device include Apple iOS, Apple OS X, Google Android, Google Chrome OS, Microsoft Windows, or Microsoft Windows Phone.
Keep in mind, this isn't the first time Facebook has explored ways of manipulating its users. In 2014, Facebook ran a social experiment exploiting the emotions of nearly 700,000 users to determine whether negative or positive content would impact their emotions, in which it has been established to be very effective (Kramer, Guillory & Hancock, 2014). Whether this technology will be implemented or not, in the meantime, it may be best to put tape over your devices' cameras, unless you would prefer to participate, and thus consent to, the end of your right to privacy. ReferencesGrasso, S., & Baker-Whitelaw, G. (2017). Facebook patent application describes spying on users through their webcams. The Daily Dot. Retrieved 28 July 2017, from https://www.dailydot.com/debug/facebook-spy-webcam-patent-ads/ Kramer, A., Guillory, J., & Hancock, J. (2014). Experimental evidence of massive-scale emotional contagion through social networks. Proceedings Of The National Academy Of Sciences, 111(24), 8788-8790. http://dx.doi.org/10.1073/pnas.1320040111 TECHNIQUES FOR EMOTION DETECTION AND CONTENT DELIVERY - FACEBOOK, INC.. (2017). Freepatentsonline.com. Retrieved 28 July 2017, from http://www.freepatentsonline.com/y2015/0242679.html In the wake of London and Manchester, politicians around the world are trying to convince the public that the free flow of information on the internet is a terror threat. In reality, independent online media are exposing the real terrorists: the politicians and their deep state handlers who are funding, arming, aiding and enabling false flag terror.
|
This feed contains research, news, information, observations, and ideas at the level of the world.
Archives
May 2024
Categories
All
|
||||||||||||



 RSS Feed
RSS Feed

