|
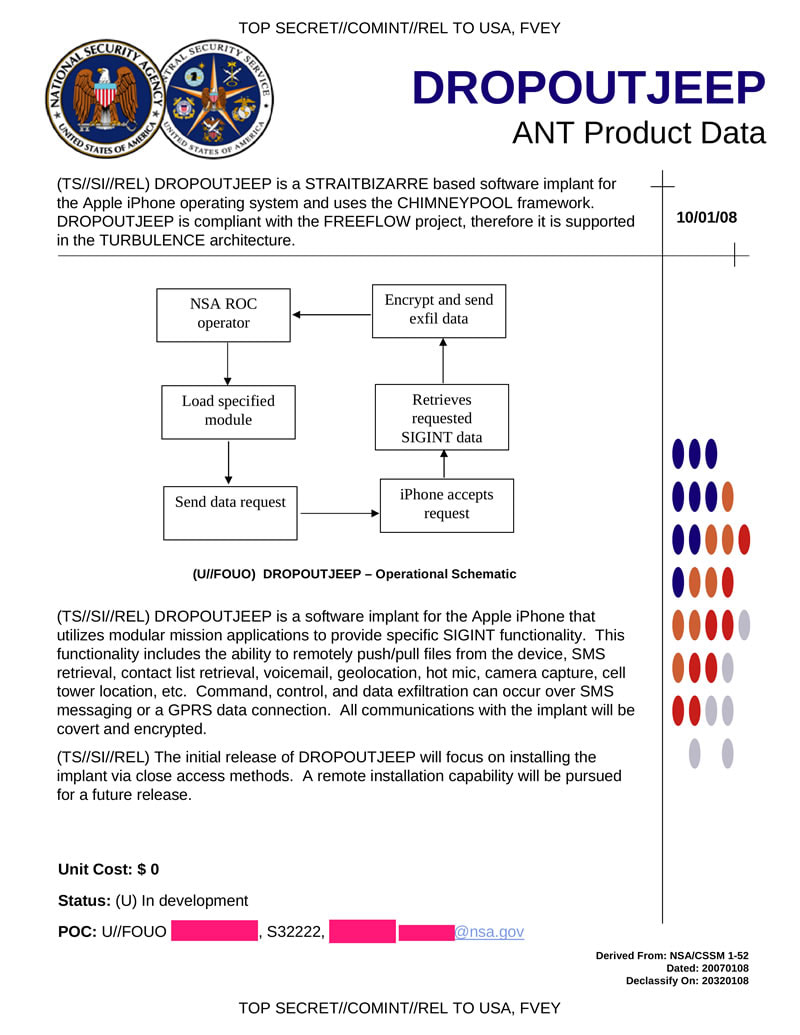
If you haven't already been informed, the new iPhone X was announced September 12, 2017. While the $1,000 device represents a whole new era of technological achievement, many of the new capabilities should raise some concern. Most notable is Face ID; the ability to unlock the device with the user's face and eyes. This feat is accomplished by a number of new sensors built into the front-facing screen, including a dot projector, infrared camera, flood illuminator and proximity sensor. By projecting a field of over 30,000 invisible dots out into the environment, together these sensors are able to constantly scan for and map the geometry of the user's face to unlock the device from multiple angles, even in the dark. In other words, your face is your password. The technology is able model faces and adapt to the changing landscape and aspects of a person’s face as they grow and change. Apple states that the biometric data is stored locally on the device and claims that Face ID cannot be fooled by photographs of faces. Beyond the obvious question, "why is this necessary?", delving deeper into the device and it's data ties with the intelligence agencies, should raise skepticism regarding the true intentions behind the technology. Privacy Violation: Governments Spying Via iPhones According to hundreds of leaked documents via Wikileaks, as many as 160 intelligence contractors in the mass surveillance industry may have access to the data on a single cellular device. Intelligence agencies, military forces and police authorities are able to silently, and on mass, and secretly intercept calls and take over computers without the help or knowledge of the telecommunication providers - no matter the country. Users’ physical location can be tracked if they are carrying a mobile phone, even if it is only on stand by. In addition, systems to infect every Facebook user, or smart-phone owner of an entire population group are and have been on the intelligence market since the rise of the patriot act, due to events that took place on September 11, 2001. Companies like Phoenexia in the Czech Republic collaborate with the military to create speech analysis tools. These speech analysis tools are able to identify individuals by gender, age and stress levels and track them based on ‘voiceprints’. DROPOUTJEEP, a spyware said to be one of the tools employed by the NSA's ANT (Advanced or Access Network Technology) division, is able to gain backdoor access to various electronic devices. DROPOUTJEEP can infiltrate virtually all areas of the iPhone (not only the iPhone X), including voice mail, contact lists, instant messages, and cell tower location. The general response among people who have justified and have been normalized to privacy violation after reading this is, "I have nothing to hide." Why is it that one closes the door when they use the restroom? Or why does one have a password on their phone is the first place? Akin to freedom of speech, privacy is, or should be, a basic human right. But the reality is that the right to privacy no longer exists. By waiving your freedom of privacy and saying, "I have nothing to hide", is equivalent to waiving your freedom of speech and saying, "I have nothing to say." Normalizing Facial Scanning Have you had your fingerprints taken for government ID? Your irises scanned? Your earlobes measured? A microchip implanted? Are you prepared to? Where will you draw the line? Acknowledged or not, this technology is normalizing facial scanning. Let us not be naive, this is a coordinated plan to institute a worldwide biometric id system to track every human on the planet. Faces Contain a Significant Amount of Data The science of judging one’s character from their facial characteristics, or physiognomy, dates back to ancient China and Greece. Aristotle and Pythagoras were among its disciples, and the latter used to select his students based on their facial features. Cesare Lombroso, the founder of criminal anthropology, believed that criminals could be identified by their facial features. There is a growing body of evidence suggesting that character can influence one’s facial appearance, and vice versa. The appearance of an individual's face drives first impressions of others, influencing our expectations and behavior toward them, which, in turn, shapes their character. The existence of such links between facial appearance and character is supported by the fact that people can accurately judge others’ character, psychological states, and demographic traits from their faces. Some people can easily and accurately identify others’ gender, age, race, or emotional state — even from a glimpse of their faces. However others may lack the ability to detect or interpret them. Case in point, a patent filed in 2014 by Facebook described plans to detect users emotions and deliver specific content, based on those emotions, through computing devices such as laptops, mobile phones and tablets that have a digital camera. Recent progress in AI and computer vision has been largely driven by the widespread adoption of deep neural networks (DNN), or neural networks composed of a large number of hidden layers. DNNs mimic the neocortex by simulating large, multi-level networks of interconnected neurons. DNNs excel at recognizing patterns in large, unstructured data such as digital images, sound, or text, and analyzing such patterns to make predictions. DNNs are increasingly outperforming humans in visual tasks such as image classification, facial recognition, or diagnosing skin cancer. The superior performance of DNNs offers an opportunity to identify links between characteristics and facial features that might be missed or misinterpreted by the human brain. Michal Kosinski, a Stanford University professor, conducted research suggesting that artificial intelligence (AI) can detect the sexual orientation of people based on photos. He mentions that sexual orientation was just one of many characteristics that algorithms would be able to predict through facial recognition. Using photos, AI will be able to identify people’s political views, whether they have high IQs, whether they are predisposed to criminal behavior, whether they have specific personality traits and many other private, personal details that could carry huge social consequences, he said. Faces contain a significant amount of information, and using large datasets of photos, sophisticated computer programs can uncover trends and learn how to distinguish key traits with a high rate of accuracy. With Kosinski’s AI, an algorithm used online dating photos to create a program that could correctly identify sexual orientation 91% of the time with men and 83% with women, just by reviewing a handful of photos. A Feature Able to be Used Against One's Will The iPhone X’s facial recognition capabilities could spell disaster for those wanting to keep their private data from the prying eyes of law enforcement. While the convenience of not having to lift a finger to unlock a phone is being touted as a selling point by Apple, the potential for privacy invasion at the hands of police has people worried. Police require a warrant to unlock and check your phone, but they don’t need one to compel you to use your fingerprint to unlock it. Run through the following scenario: Police demand access to your iPhone X. Cannot compel you without warrant? No problem, they turn phone to face you, unlocks with FaceID. In 2014, a Virginia judge ruled police could force users to unlock their phones using their fingerprints. In February 2016, a judge in Los Angeles signed a search warrant to make a woman unlock her iPhone with her fingerprint. Due to Fifth Amendment protections around self-incrimination in the US, police can’t force a person to give over their passcode, as it’s considered “knowledge.” Albeit, a fingerprint or a face, however, is a different scenario. This is worrying for the vast amount of people who are unlawfully detained and illegally searched. Data Being Used Against the User Beyond the violation of privacy, there are larger implications by which the intelligence agencies are able to hijack individual computers and phones (including iPhones, Blackberries and Androids), take over the device, record its every use, movement, and even the sights and sounds of the room it is in. With the help of this facility, and many others like it, each day the NSA is able to intercept and store 1.7 billion electronic communications. Since it's inception, this secret industry has boomed and is worth billions of dollars per year. There are commercial firms that now sell special software that analyze this data and turn it into powerful tools that can be used by military and intelligence agencies. Around the world, mass surveillance contractors are helping intelligence agencies spy on individuals and ‘communities of interest’ on an industrial scale. The Wikileaks Spy Files reveal the details of which companies are making billions selling sophisticated tracking tools to government buyers, flouting export rules, and turning a blind eye to dictatorial regimes that abuse human rights. Sentient World Simulation
Remarkably, this is precisely what is happening. It is called the “Sentient World Simulation.” The program’s aim, according to its creator, is to be a “continuously running, continually updated mirror model of the real world that can be used to predict and evaluate future events and courses of action.” In practical terms that equates to a computer simulation of the planet complete with billions of “nodes” representing every person on the earth. The project is based out of Purdue University in Indiana at the Synthetic Environment for Analysis and Simulations Laboaratory. It is led by Alok Chaturvedi, who in addition to heading up the Purdue lab also makes the project commercially available via his private company, Simulex, Inc. which boasts an array of government clients, including the Department of Defense and the Department of Justice, as well as private sector clients like Eli Lilly and Lockheed Martin. The program can be used to predict what would happen in the event of a large scale tsunami, for example, or how people would react during a bioterror attack. Businesses can use the models to predict how a new product would fare in the market, what kind of marketing plans would be most effective, or how best to streamline a company’s organization. The original concept paper for the project was published in 2006 and in 2007 it was reported that both Homeland Security and the Defense Department were already using the system to simulate the American public’s reaction to various crises. In the intervening five years, however, there has been almost no coverage at all of the Sentient World Simulation or its progress in achieving a model of the earth. The Sentient World Simulation is one example of one program run by one company for various governmental and Fortune 500 clients. But it is a significant peek behind the curtain at what those who are really running our society want: complete control over every facet of our lives achieved through a complete invasion of everything that was once referred to as “privacy.” Ultimately, it should be noted that all technology can be used as either a tool or as a weapon. But when the technology is in the hands of multinational, monopoly corporations with government influences and coercion, it may be best to side with skepticism and not with open arms. ReferencesCorbett, J. (2012). Sentient World Simulation: Meet Your DoD Clone : The Corbett Report. [online] Corbettreport.com. Available at: https://www.corbettreport.com/sentient-world-simulation-meet-your-dod-clone/ [Accessed 24 Sep. 2017]. Krannert.purdue.edu. (2017). Seas Labs. [online] Available at: http://www.krannert.purdue.edu/centers/perc/html/aboutperc/seaslabs/seaslabs.htm [Accessed 24 Sep. 2017]. Priest, D. and Arkin, W. (2010). A hidden world, growing beyond control (Printer friendly version)| washingtonpost.com. [online] Projects.washingtonpost.com. Available at: http://projects.washingtonpost.com/top-secret-america/articles/a-hidden-world-growing-beyond-control/print/ [Accessed 24 Sep. 2017]. RT International. (2017). iPhone X facial recognition could give cops easy access to your cell. [online] Available at: https://www.rt.com/news/403229-iphone-face-id-police/ [Accessed 24 Sep. 2017]. Wang, Y., & Kosinski, M. (2017). Deep neural networks are more accurate than humans at detecting sexual orientation from facial images. Journal of Personality and Social Psychology Wikileaks.org. (2014). WikiLeaks - The Spy Files. [online] Available at: https://wikileaks.org/the-spyfiles.html [Accessed 15 Sep. 2017].
0 Comments
In the details of the document, air temperature within the eye and in the outflow of a hurricane is able to be raised by flying scores of jet planes with afterburners in the structure. It should be noted that small changes in temperature on a large scale bring in large changes in other variables on the smaller scale to change the direction and intensity of the hurricane. BackgroundCloud seeding is a known process for artificially modifying the weather by injecting a composition into a cloud for formation of an ice freezing nuclei. Silver iodide is a well known substance used for cloud seeding. The Storm fury project carried out by the US Government for several years focused on hurricane formation suppression by means of aerial dispersion of silver iodide. This project was evaluated as a failure and cancelled. In 1976, William Gray et al., suggested that the use of carbon black (or soot) might be a good way to modify tropical cyclones. The idea was that one could burn a large quantity of a heavy petroleum to produce vast numbers of carbon black particles that would be released on the edges of the tropical cyclone in the boundary layer. These carbon black aerosols would produce a heat source simply by absorbing the solar radiation and transferring the heat directly to the atmosphere. This would provide for the initiation of thunderstorm activity outside of the tropical cyclone core and weaken the eye wall convection. In 1958, the US Naval Research laboratory carried out some experiments to monitor clouds seeded with soot but the results were inconclusive. Advantages As described in the patent, there are several "advantages", for the existence and application of this technology:
Patents Related to Weather Modification Below is a list composed of some of the patents that describe abilities to modify weather:
References
Project Popeye - Cloud Seeding During Vietnam War
Project Popeye was a highly classified weather modification program in Southeast Asia during 1967–1972. The objective of the program was to produce sufficient rainfall along these lines of communication to interdict or at least interfere with truck traffic between North and South Vietnam.
A test phase of Project Popeye was approved by State and Defense and conducted during October 1966 in a strip of the Lao Panhandle generally east of the Bolovens Plateau in the valley of the Se Kong River. The test was conducted without consultation with Lao authorities (but with Ambassador Sullivan’s knowledge and concurrence). During the test phase, more than 50 cloud seeding experiments were conducted. The results are viewed by DOD as outstandingly successful.
The experiments were deemed undeniably successful, indicating that, at least under weather and terrain conditions such as those involved, the U.S. Government has realized a capability of significant weather modification. If anything, the tests were “too successful”—neither the volume of induced rainfall nor the extent of area affected can be precisely predicted (Department of State - Office of the Historian, 1967). Project Stormfury - An Attempt to Modify Hurricanes
Project Stormfury was an attempt to weaken tropical cyclones by flying aircraft into them and seeding with silver iodide.
The project was run by the United States Government from 1962 to 1983.The hypothesis was that the silver iodide would cause supercooled water in the storm to freeze, disrupting the inner structure of the hurricane. This led to the seeding of several Atlantic hurricanes. However, it was later shown that this hypothesis was incorrect. In reality, it was determined most hurricanes do not contain enough supercooled water for cloud seeding to be effective. Additionally, researchers found that unseeded hurricanes often undergo the same structural changes that were expected from seeded hurricanes. This finding called Stormfury’s successes into question, as the changes reported now had a natural explanation. The last experimental flight was flown in 1971, due to a lack of candidate storms and a changeover in NOAA’s fleet. More than a decade after the last modification experiment, Project Stormfury was officially canceled. Although a failure in its goal of reducing the destructiveness of hurricanes, Project Stormfury was not without merit. The observational data and storm lifecycle research generated by Stormfury helped improve meteorologists’ ability to forecast the movement and intensity of future hurricanes. Former CIA Director, John Brennan, Discusses SAI or "Chemtrails"
A number of government agencies have developed plans for research and operational programs in weather and climate modification. Here is a report from 1966, in which various agencies expressed interest in the ability to modify the weather. In 2015, the National Academy of Sciences conducted a 21-month geoengineering study, which happened be funded by the "U.S Intelligence community", also known as the Central Intelligence Agency (National Academy of Sciences, 2015). Below is a video of John Brennan, former CIA director from March 2013 to January 2017, speaking about stratospheric aerosol injection (SAI), commonly referred to as "chemtrails", at the Council on Foreign Relations.
Research Suggests Climate Engineering is Ineffective
Scientists at Helmholtz Centre for Ocean Research (Kiel, Germany) conducted a study where they evaluated effectiveness and risks of different geoengineering techniques, such as SRM (solar radiation management), afforestation, artificial ocean upwelling, ocean iron fertilization and ocean alkalinization.
The researchers discovered that even when applied continuously and at scales as large as currently deemed possible, all methods are, individually, either relatively ineffective with limited (o8%) warming reductions, or they have potentially severe side effects and cannot be stopped without causing rapid climate change (Keller, Feng and Oschlies, 2014). To assess their true potential and verify their side effects, such interventions require full-scale experiments that may have long-term and possibly compromise the very planetary mechanisms and ecosystems we’re trying to save. Potential Proof of Weather Manipulation
In the photos below, several abnormal cloud formations with a seemingly unnatural origin, containing straight lines and 90° angles, can be observed.
Based on the information aforementioned, toxic materials, heavy metals, and harmful chemicals are able to be positioned in the atmosphere of the planet. Many speculate that these particles may be manipulated by powerful radio frequency signals, in which a strange impact on clouds can be observed. In addition, it is claimed that these square clouds are created via electrically conductive heavy metal nanoparticles (that are constantly being sprayed into our atmosphere by the the geoengineers) which are able to be manipulated with the global grid of radio frequency transmitters. Some suggest that these radio frequencies have originated from ionospheric heaters like HAARP (High Frequency Active Auroral Research Program) in Gakona, Alaska, the most notable U.S. geoengineering facility. HAARP wasscheduled for shut down by the U.S. Air Force in May, 2014. There are many other transmission installations around the world, some officially known and others completely secret. U.S. Senate Document Reveals Weather Modification
The United States Federal government has been involved for over 60 years in a number of aspects of weather modification, through activities of both the Congress and executive branch. Since 1947, weather modification bills pertained to research support, operations, policy studies, regulations, liabilities, activity reporting, establishment of panels and committees, and international concerns have been introduced in the Congress. There have been hearings on many of these proposed measures, and oversight hearings have also been conducted on pertinent ongoing programs. In the 750-page document below, various topics regarding weather modification are discussed, including but not limited to:
Weather Warfare Explained Further
References
Department of State - Office of the Historian. (1967). Foreign Relations of the United States, 1964–1968, Volume XXVIII, Laos - Office of the Historian. [online] Available at: https://history.state.gov/historicaldocuments/frus1964-68v28/d274#fnref:1.5.4.4.14.336.7.6 [Accessed 12 Sep. 2017].
Keller, D., Feng, E. and Oschlies, A. (2014). Potential climate engineering effectiveness and side effects during a high carbon dioxide-emission scenario. Nature Communications, 5. https://doi.org/10.1038/ncomms4304 Wigington, D. (2016). Is Climate Engineering Real? Square Cloud Formations Are Undeniable Proof. [online] Geoengineering Watch. Available at: http://www.geoengineeringwatch.org/is-climate-engineering-real-square-cloud-formations-are-undeniable-proof/ [Accessed 12 Sep. 2017].
Transcript:
Forget for one moment everything you’ve been told about September 11, 2001. Instead let’s ask ourselves one question: What was 9/11? A terrorist atrocity? An attack on America? The first salvo in a new war? “A day that changed everything”? The question may seem simple, but how we answer it is of vital importance. It determines how we proceed with our investigation of that day. And once you strip away the emotional rhetoric and the fear-inducing imagery, we’re left with a simple truth: 9/11 was a crime. And as with any crime, there is one overriding imperative that detectives must follow to identify the perpetrators: Follow the money. This is an investigation of the 9/11 money trail. The 9/11 Heist In 1998, the Port Authority of New York and New Jersey agreed to privatize the World Trade Center, the complex of office towers in Lower Manhattan that they had owned and operated since their construction in 1973. In April 2001 an agreement was reached with a consortium of investors led by Silverstein Properties, and on July 24th, 2001, Larry Silverstein, who already owned World Trade Center Building 7, signed a 99-year lease for the Twin Towers and Buildings 4 and 5. The lease was for $3.2 billion and was financed by a bridge loan from GMAC, the commercial mortgage arm of General Motors, as well as $111 million from Lloyd Goldman and Joseph Cayre, individual real estate investors. Silverstein Properties only put down $14 million of its own money. The deal was unusual in a variety of ways. Although the Port Authority carried only $1.5 billion of insurance coverage on the WTC complex, which earlier that year had been valued at $1.2 billion, Silverstein had insisted on doubling that amount, insuring the buildings for $3.55 billion. Silverstein’s insurance broker struggled to put that much coverage in place and ultimately had to split it among 25 dealers. The negotiations were so involved that only temporary contracts were in place for the insurance at the time the lease was signed, and by September the contracts were still being finalized. Silverstein’s group was also explicitly given the right to rebuild the structures if they were destroyed—and even to expand the amount of retail space on the site if rebuilding did take place. Within hours of the destruction of the Twin Towers on September 11th, Silverstein was on the phone to his lawyers, trying to determine if his insurance policies could “construe the attacks as two separate, insurable incidents rather than one.” Silverstein spent years in the courts attempting to win $7.1 billion from his $3.55 billion insurance policy and in 2007 walked away with $4.55 billion, the largest single insurance settlement ever. As soon as the deal was announced, Silverstein sued United and American Airlines for a further $3.5 billion for their “negligence” in the 9/11 attacks, a claim that was struck down by the courts but is still on appeal. Perhaps even more outrageously, in a secret deal in 2003, the Port Authority agreed to pay back 80% of their initial equity in the lease, but allowed the Silverstein group to maintain control of the site. The deal gave Silverstein, Goldman and Cayre $98 million of the $125 million they put down on the lease, and a further $130 million in insurance proceeds that were earmarked for the site’s rebuilding. In the end, Silverstein profited from the 9/11 attacks to the tune of $4.55 billion and counting. But that’s the 9/11 insurance heist you saw. There was a much deeper, more complex, and well-hidden heist that was taking place behind closed doors on September 11, 2001, deep in the heart of the World Trade Center itself. Marsh & McLennan is a diversified risk, insurance and professional services firm with over $13 billion in annual revenue and 57,000 employees. In September of 2001, 2,000 of those employees worked in Marsh’s offices in the World Trade Center. Marsh occupied floors 93 to 100 of the North Tower, the exact area of the impact and explosion. In the year prior to 9/11, Marsh had contracted with SilverStream software to create an electronic connection between Marsh and its clients for the purpose of creating “paperless transactions.” SilverStream had already built internet-based transactional and trading platforms for Merrill Lynch, Deutsche Bank, Banker’s Trust, Alex Brown, Morgan Stanley and other financial services firms that were later involved in 9/11, but this new project was unlike anything that had been attempted before. Richard Andrew Grove, the salesperson who handled the Marsh & McLennan project for SilverStream, explains. RICHARD GROVE: In 2000 SilverStream was contracted by Marsh to provide a technological solution beyond what we had done for any of the above-named companies; insofar as it would be used to electronically connect Marsh to its major business partners via internet portals, for the purpose of creating “paperless transactions” and expediting revenue and renewal cycles, and built from the ground up at the client’s site. SilverStream provided a specific type of connectivity that was used to link AIG and Marsh & McLennan—the first two commercial companies on the planet to employ this type of transaction—and in fact Marsh was presented with something called the ACORD Award in the summer of 2001 for being the first commercial corporation to do so…. And what you should take away from that is this: it means that no other companies were doing this type of transaction. So the question in your mind should be: What then were Marsh and AIG doing, and why did they need to leverage technologies that no other commercial entity on the face of the earth needed to conduct business? Once securing the contract, SilverStream then stationed approximately 30-to-40 developers at Marsh, and this team was led by two-to-three managers, with whom I liaised to ensure delivery of the “solution” that was promised. The development team regularly worked late into the night, if not all night, and sometimes worked seven days a week in order to adhere to Marsh’s indicated pre-September 11th deadline. (SOURCE: Project Constellation) But it was not long before severe irregularities in the billing of the account for this project led Richard Grove into the heart of a deeper mystery about the software, and about the work he was engaged in. RICHARD GROVE: I first noticed fiscal anomalies with respect to the Marsh.com project, when I was in a meeting on the 98th floor in October of 2000 with a gentleman named Gary Lasko. Gary was Marsh’s North American Chief Information Officer, and that particular afternoon a colleague and I helped him identify about $10,000,000 in suspicious purchase orders—after I recognized that certain vendors were deceiving Marsh, and specifically appeared to be selling Marsh large quantities of hardware that were not necessary, as this was later confirmed by Gary. I brought my concerns up to executives inside of SilverStream, and I was urged to keep quiet and mind my own business. I went to an executive at Marsh, and he advised me to do likewise…. But then I mentioned it to a few executives at Marsh whom I could trust—ike Gary Lasko…and Kathryn Lee, Ken Rice, Richard Breuhardt, John Ueltzhoeffer—people who became likewise concerned that something untoward was going on. The concerned colleagues I just mentioned were murdered on September 11th, and the executives who expressed dismay at my concerns are alive and free today because of it. I feel that it’s no coincidence, as the Marsh executive who urged me to drop my line of inquiry made sure that his personnel, who I just mentioned, were in the office bright and early for a global conference call before the staff meeting upon which I was to intrude—a conference call which I was informed this executive in question conducted but attended from the safety of his Upper West Side apartment. (SOURCE: Project Constellation) The global conference call with Marsh’s IT staff on the morning of 9/11, a meeting that included the staff who were investigating the suspicious billing on the SilverStream deal, was confirmed in a 2006 interview with Marsh’s then-Chief Information Officer, Ellen Clarke. Richard Grove had been asked to attend the meeting but was stuck in traffic on the way to the Towers when the attack began. His friends at Marsh were not so lucky: 294 Marsh employees, including all of the participants in the conference call in the North Tower, died that morning. Meanwhile the Marsh executive who had scheduled the meeting, the same one who had asked Grove to drop the issue of the billing anomalies, was safe in his apartment, attending the meeting via telephone. So what was the Marsh.com project really about? Why was it so important for it to be finished before September 11th, and what kind of transactions did it enable? More importantly, what information was lost when the data center on the 95th floor of the North Tower suffered a direct hit on 9/11 and the buildings were demolished? A partial answer comes from reports that emerged in late 2001: that a German firm, Convar, had been hired to reconstruct financial data from the hard disks recovered at Ground Zero. The firm talks about this work in its promotional videos. September the 11th, 2001. The whole world is in shock following the attacks on the World Trade Center. Convar has some solutions to offer. Data stored on countless hard drives retrieved from the collapsed towers was believed to have been lost, but Convar’s specialists can render irreplaceable information readable again at Europe’s only high-security data recovery center. Burnt, crushed or dirty storage media are ready to relinquish their secrets by the time we finish. (SOURCE: CONVAR – Repair & Service Center) More details on the work come from an IDG News Service story posted to CNN.com in December 2001. Under the headline “Computer disk drives from WTC could yield clues,” the article notes: “An unexplained surge in transactions was recorded prior to the attacks, leading to speculation that someone might have profited from previous knowledge of the terrorist plot by moving sums of money. But because the facilities of many financial companies processing the transactions were housed in New York’s World Trade Center, destroyed in the blasts, it has until now been impossible to verify that suspicion.” A Reuters article from the same time, later posted to Convar’s website, offers revealing glimpses into the investigation’s early results. It quotes Peter Herschel, Convar’s director at the time. “The suspicion is that inside information about the attack was used to send financial transaction commands and authorizations in the belief that amid all the chaos the criminals would have, at the very least, a good head start. Of course it is also possible that there were perfectly legitimate reasons for the unusual rise in business volume. It could turn out that Americans went on an absolute shopping binge on that Tuesday morning. But at this point there are many transactions that cannot be accounted for. Not only the volume but the size of the transactions was far higher than usual for a day like that. There is a suspicion that these were possibly planned to take advantage of the chaos.” It also quotes Richard Wagner, one of the companies data retrieval experts. “There is a suspicion that some people had advance knowledge of the approximate time of the plane crashes in order to move out amounts exceeding $100 million. They thought that the records of their transactions could not be traced after the mainframes were destroyed.” Was the revolutionary electronic trading link between AIG and Marsh being used to funnel money through the World Trade Center at the time of the attack? Were the attack perpetrators hoping that the destruction of Marsh’s data center, on the 95th floor at the dead center of the North Tower explosion, would conceal their economic crime? One piece of corroborating evidence for this idea comes from author and researcher Michael Ruppert, who reported in 2004 that immediately before the attacks began, computer systems in Deutsche Bank, one of SilverStream’s other e-link clients, had been taken over from an external location that no one in the office could identify. MICHAEL RUPPERT: Within, I would guess — I’d have to go back and look at the book, but it was no more than a week of the attacks — I was being contacted by a lot of people, from inside official sources who were raising a lot of questions. This one particular person was extremely credible. They absolutely convinced me they had been an employee of Deutsche Bank in the Twin Towers, and they told me very clearly that in the moments right before the attacks and during the attack — there was a 40-minute window between the time the first plane struck the World Trade Center and the second plane — that Deutsche Bank’s computers in New York City had been “taken over.” Absolutely co-opted and run. There was a massive data purge, a massive data download, and all kinds of stuff was moving. And what this person said very clearly was that no one in the Deutsche Bank offices in the towers at the time had the ability to prevent what was going on from any of their terminals. (SOURCE: Terror Trading 9/11) Sadly, no answer to the questions raised by these accounts is forthcoming from Convar. After the initial reporting on the investigation, which noted that the company was working with the FBI to recover and analyze the data, Convar now refuses to talk about the information they discovered. DUTCH REPORTER: Is it true that large amounts of money were transferred illegally out of the World Trade Center on the morning of 9/11, just before the attacks? CONVAR SPOKESMAN: If you would look on the website, I would say “Yes.” DUTCH REPORTER: Uh huh. CONVAR SPOKESMAN: Because that was the information from a previous release. DUTCH REPORTER: Uh huh. CONVAR SPOKESMAN: If you were to ask me today I would need to tell you I could not give you any additional information about that. I’m really sorry about… DUTCH REPORTER: What if I were to ask you one year ago? What would you have… CONVAR SPOKESMAN: I would have said that what we have there is what we said before. Yes, exactly. (SOURCE: Dutch TV show Zembla investigates 9/11 theories) At the time of 9/11, Marsh’s chief of risk management was Paul Bremer, the former managing director of Kissinger and Associates who went on to oversee the US occupation of Iraq. On the morning of 9/11 he was not in his office at Marsh & MacLennan, but at NBC’s TV studio, where he was delivering the official story of the attack. NBC4 ANCHOR #1: Can you talk to us a little bit about…about…who could…I mean, there are a limited number of groups who could be responsible for something of this magnitude, correct? PAUL BREMER: Yes, this is a very well-planned, very well-coordinated attack, which suggests it is very well-organized centrally, and there are only three or four candidates in the world really who could have conducted this attack. NBC4 ANCHOR #2: Bin Laden comes to mind right away, Mr. Bremer. PAUL BREMER: Indeed, he certainly does. Bin Laden was involved in the first attack on the World Trade Center which had as its intention doing exactly what happened here, which was to collapse both towers. He certainly has to be a prime suspect. But there are others in the Middle East, and there are at least two states, Iran and Iraq, which should at least remain on the list of potential suspects. NBC4 ANCHOR #2: I don’t recall anything like this. Pearl Harbor happened a month before I was born and I hear my parents talk about that as a seminal event in their lives all the time. I’m not aware of anything like this in the United States before. Americans are now — I think it’s fair to say — really scared. Should we be? NBC4 ANCHOR #1: This is a day that will change our lives, isn’t it? PAUL BREMER: It is a day that will change our lives, and it’s a day when the war that the terrorists declared on the United States — and after all, they did declare a war on us — has been brought home to the United States in a much more dramatic way than we’ve seen before, so it will change our lives. (SOURCE: Paul Bremer interview, NBC) 9/11 Insider Trading On September 12, 2001, before the dust had even settled on Ground Zero, the Securities and Exchange Commission opened an investigation into a chilling proposition: that an unknown group of traders with advance knowledge of the 9/11 plot had made millions betting against the companies involved in the attacks. ANTONIO MORA: “What many Wall Street analysts believe is that the terrorists made bets that a number of stocks would see their prices fall. They did so by buying what they call ‘puts.’ If you bet right the rewards can be huge. The risks are also huge unless you know something bad is going to happen to the company you’re betting against. DYLAN RATIGAN: This could very well be insider trading at the worst, most horrific, most evil use you’ve ever seen in your entire life. ANTONIO MORA: One example, United Airlines. The Thursday before the attack more than two thousand contracts betting that the stock would go down were purchased. Ninety times more in one day than in three weeks. When the markets reopened, United’s stock dropped, the price of the contracts soared, and someone may have made a lot of money, fast. DYLAN RATIGAN: $180,000 turns into $2.4 million when that plane hits the World Trade Center. ANTONIO MORA: It’s almost the same story with American Airlines. DYLAN RATIGAN: That’s a fivefold increase in the value of what was a $337,000 trade on Monday (September 10, 2001). ANTONIO MORA: All of a sudden becomes what? DYLAN RATIGAN: $1.8 million. ANTONIO MORA: And there’s much more, including an extraordinarily high number of bets against Morgan Stanley and Marsh & McLennan, two of the World Trade Center’s biggest tenants. Could this be a coincidence? DYLAN RATIGAN: This would be one of the most extraordinary coincidences in the history of mankind if it was a coincidence.” (SOURCE: 9/11 Wall Street Blames Put Option Inside Trading On Terrorists) Although the put options on American and United Airlines are usually cited in reference to the 9/11 insider trading, these trades only represent a fraction of the suspicious trades leading up to the attack. Between August 20th and September 10th, abnormally large spikes in put option activity appeared in trades involving dozens of different companies whose stocks plunged after the attack, including Boeing, Merrill Lynch, J.P. Morgan, Citigroup, Bank of America, Morgan Stanley, Munich Re and the AXA Group. Traders weren’t just betting against the companies whose stocks dove after 9/11, however. There was also a sixfold increase in call options on the stock of defense contractor Raytheon on the day before 9/11. The options allowed the traders to buy Raytheon stock at $25. Within a week of the attack, as the American military began deploying the Raytheon-supplied Tomahawk missiles they would eventually use in the invasion of Afghanistan, the company’s share price had shot up 37% to over $34. The SEC weren’t the only ones interested in this particular 9/11 money trail, either. Investigations into potential insider trading before the attacks were opened by authorities around the globe, from Belgium to France to Germany to Switzerland to Japan. It wasn’t long before this global financial manhunt started yielding clues on the trail of the terror traders. On September 17th, Italian Foreign Minister Antonio Martino, addressing Italian Consob’s own investigation into potential 9/11 trading, said: “I think that there are terrorist states and organizations behind speculation on the international markets.” By September 24th, the Belgian Finance Minister, Didier Reynders, was confident enough to publicly announce Belgium’s “strong suspicions that British markets may have been used for transactions.” The president of Germany’s central bank, Ernst Welteke, was the most adamant: “What we found makes us sure that people connected to the terrorists must have been trying to profit from this tragedy.” These foreign leaders were not alone in their conviction that insider trading had taken place. University of Chicago finance professor George Constantinides, Columbia University law professor John Coffee, Duke University law professor James Cox and other academics as well as well-known options traders like Jon Najarian all expressed their belief that investors had traded on advance knowledge of the attacks. The scale of the SEC investigation was unprecedented, examining over 9.5 million securities transactions, including stocks and options in 103 different companies trading in seven markets, 32 exchange-traded funds, and stock indices. The probe drew on the assistance of the legal and compliance staff of the 20 largest trading firms and the regulatory authorities in ten foreign governments. The Commission coordinated its investigation with the FBI, the Department of Justice, and the Department of the Treasury. The result of this investigation? “We have not developed any evidence suggesting that those who had advance knowledge of the September 11 attacks traded on the basis of that information.” Although this sounds like the investigation did not find evidence of insider trading, a second look reveals the trick; they are not saying that there was no insider trading, only that there is no evidence that “those who had advance knowledge of the September 11 attacks” participated in such trading. But this begs the question: Who had that advance knowledge, and how did the SEC determine this? The 9/11 Commission Report begs the question even more blatantly in their treatment of the anomalous put option activity on United Airlines stock on September 6: 95% of the puts were placed by “a single U.S.-based institutional investor with no conceivable ties to al Qaeda.” Again, it is taken as a foregone conclusion that a lack of ties to “al Qaeda” means there could not have been advance knowledge of the attack, even if the evidence shows insider trading took place. To be sure, insider trading almost certainly did take place in the weeks before 9/11. Although some have used the Commission report to conclude that the story was debunked, the intervening years have seen the release of not one, not two, but three separate scientific papers concluding with high probability that the anomalous trading was the result of advance knowledge. In “Unusual Option Market Activity and the Terrorist Attacks of September 11, 2001,” University of Chicago professor Allen Poteshman concluded: “Examination of the option trading leading up to September 11 reveals that there was an unusually high level of put buying. This finding is consistent with informed investors having traded options in advance of the attacks.” In “Detecting Abnormal Trading Activities in Option Markets,” researchers at the University of Zurich used econometric methods to confirm unusual put option activity on the stocks of key airlines, banks and reinsurers in the weeks prior to 9/11. And in “Was There Abnormal Trading in the S&P 500 Index Options Prior to the September 11 Attacks?” a team of researchers concluded that abnormal activity in the S&P index options market around the time of the attack “is consistent with insiders anticipating the 9-11 attacks.” The only question, then, is who was profiting from these trades and why was no one ever indicted for their participation in them? One lead is pursued by researcher and author Kevin Ryan. In “Evidence for Informed Trading on the Attacks of September 11,” he examines an FBI briefing document from 2003 that was declassified in 2009. It describes the results of FBI investigations into two of the pre-9/11 trades that the Bureau had identified as suspicious, including the purchase of 56,000 shares of Stratesec in the days prior to 9/11. Stratesec provided security systems to airports (including, ironically, Dulles Airport, as well as the World Trade Center and United Airlines) and saw its share price almost double when the markets re-opened on September 17th, 2001. The trades traced back to a couple whose names are redacted from the memo, but are easily identifiable from the unredacted information: Mr. and Mrs. Wirt D. Walker III, a distant relative of the Bush family and business partner of Marvin Bush, the President’s brother. The document notes that the pair were never even interviewed as part of the investigation because it had “revealed no ties to terrorism or other negative information.” In addition to begging the question, this characterization is provably false. As Ryan noted in a conversation with financial journalist Lars Schall: KEVIN RYAN: “Wirt Dexter Walker at Stratesec hired several people from a company called The Carlyle Group, and The Carlyle Group had Bin-Laden family members as investors. Also Wirt Walker’s fellow (inaudible) director James Abrahamson was a close business associate of a man named Mansoor Ijaz, a Pakistani businessman and Mansoor Ijaz claimed to be able to contact Osama Bin-Laden on multiple occasions. So there does seem to be some circumstantial evidence indicated that these people were connected to Al-Qaeda, at least to the point where we should investigate. LARS SCHALL: And isn’t it also true that some members of the Bin-Laden family were actually in Washington at the gathering of The Carlyle Group on 9/11? KEVIN RYAN: That’s true. The Carlyle Group had a meeting at the Ritz-Carlton Hotel in Washington on September 11th and present there were former President George H. W. Bush, James Baker and the brother of Osama Bin-Laden. I believe his name was Salem, I can’t recall his exact name. But they were there, investors from the Bin-Laden family meeting with Carlyle Group representatives in Washington on September 11th.” (SOURCE: Terror Trading 9/11) Was this why the FBI thought better of questioning him over his highly profitable purchase of Stratesec shares right before 9/11? The CIA figures prominently in another line of investigation. One suspicious United Airlines put option purchase that was investigated by the FBI involved a 2,500-contract order for puts in the days before 9/11. Instead of processing the purchase through United Airlines’ home exchange, the Chicago Board of Options Exchange, the order was split into five 500-contract chunks and run through five different options exhchanges simultaneously. The unusual order was brokered by Deutsch Bank Alex. Brown, a firm that until 1998 was chaired by A.B. “Buzzy” Krongard, a former consultant to CIA director James Woolsey who at the time of 9/11 was himself the Executive Director of the CIA. MICHAEL C. RUPPERT: So right after the attacks of 9/11 the name Buzzy Krongard surfaced, it was instant research that revealed that Buzzy Krongard had been allegedly recruited by CIA Director George Tennant to become the Executive Director at (the) CIA, which is the number three position, right before the attacks. And Alex Brown was one of the many subsidiaries of Deutsche Bank, (which was) one of the primary vehicles or instruments that handled all of these criminal trades by people who obviously knew that the attacks were going to take place where, how and involving specific airlines. (SOURCE: Terror Trading 9/11) Perhaps the most frank admission of insider trading is notable for three things: It was recorded on video, it has never been investigated by any agency or law enforcement official, and it was made by former CIA agent and frequent foreign policy commentator Robert Baer, the real-life inspiration for the character portrayed by George Clooney in “Syriana.” Talking to citizen journalists after a speaking event in Los Angeles in 2008, Baer was recorded on video making a startling assertion about 9/11 insider trading: JEREMY ROTHE-KUSHEL: …the last thing I want to leave you with is the National Reconnaissance Office was running a drill of a plane crashing into their building and you know they’re staffed by DoD and CIA… ROBERT BAER: I know the guy that went into his broker in San Diego and said “Cash me out, it’s going down tomorrow.” JEREMY ROTHE KUSHEL: Really? ROBERT BAER: Yeah. STEWART HOWE: That tells us something. ROBERT BAER: What? STEWART HOWE: That tells us something. ROBERT BAER: Well, his brother worked at the White House. (SOURCE: WeAreChangeLA debriefs CIA Case Officer Robert Baer about apparent Mossad and White House 9/11 foreknowledge) This truly remarkable statement bears further scrutiny. If Baer is to be believed, a former CIA agent has first-hand knowledge that a White House insider had foreknowledge of the attacks, and to this day not only has Baer never revealed the identity of this person, but no one has questioned him about his statement or even attempted to pursue this lead. So how is it possible that the SEC overlooked, ignored, or simply chose not to pursue such leads in their investigation? The only possible answer, of course, is that the investigation was deliberately steered away from such persons of interest and any connections that would lead back to foreknowledge by government agencies, federal agents, or their associates in the business world. Unfortunately, we will likely never see documentary evidence of that from the Commission itself. One researcher requesting access under the Freedom of Information Act to the documentary evidence that the 9/11 Commission used to conclude there had been no insider trading received a response that stated “that the potentially responsive records have been destroyed.” Instead, we are left with sources that refuse to be identified, saying that CBOE records of pre-9/11 options trading have been destroyed and [with] second-hand accounts of traders who had heard talk of an event in advance of 9/11. In a round-about way, perhaps the 9/11 Commission reveals more than it lets on when it tries to dismiss key insider trades with the pithy observation that the traders had no conceivable ties to Al Qaeda. If those with foreknowledge of the attacks weren’t connected to Al Qaeda, what does that say about the identity of the real 9/11 perpetrators? ANTONIO MORA: ABC News has now learned that the Chicago Board of Options Exchange launched their investigation into the unusual trading last week. That may have given them enough time to stop anyone from profiting from death here in the U.S. It may also give investigators, Peter, a “hot trail” that might lead them to the terrorists. PETER JENNINGS: Thanks very much. As a reminder of the complications here, the Secretary of the Treasury said here today of this investigation, “You’ve got to go through ten veils before you can get to the real source.” ANTONIO MORA: Yeah. PETER JENNINGS: Thanks, Antonio. (SOURCE: 9/11 Wall Street Blames Put Option Inside Trading On Terrorists) PTech and Vulgar Betrayal PTech was a Quincy, Mass.-based company specializing in “enterprise architecture software,” a type of powerful computer modeling program that allows large-scale organizations to map their systems and employees and to monitor them in real time. The person running this software has a “God’s-eye” view of processes, personnel and transactions, and even the ability to use this data to foresee problems before they happen and to intervene to stop them from happening. As a senior consultant working on risk management for JPMorgan at the time of 9/11, Indira Singh was looking for exactly this type of software to implement the bank’s next-generation risk blueprint. In her search for the ultimate risk management software, PTech’s name was floated as the best candidate for the task. INDIRA SINGH: I had a good life. I did “risk” at JP Morgan Chase, just to take a break from all the heavy stuff. What I’d do was to devise a way to monitor everything going on in a very large company to stop big problems from happening. There is that little cloud there and my very bizarre picture of how I think about this problem. I am a person who was merging two disciplines: Risk Management and something called “Enterprise Architecture” which is fairly esoteric but at the end of the day, we seek to prevent large problems from happening anywhere in a large global enterprise. At JP Morgan I was working on the next generation “risk blueprint” which is all about how to prevent these things from happening. Bad business practice such as money laundering, rogue trading and massive computer failures, anything you could imagine (that) could go wrong. I had a lot of leeway consulting as a “Senior Risk Architect” to think out of the box and actually get my ideas implemented. I was funded out of a strategic fund, I reported to the directors and I was pretty happy. JP Morgan thought very highly of me and they were thinking of funding, in conjunction with my project in D.C., the next-generation risk software. What I need to do (and) what I did was (find) a really smart piece of software. Really, really smart. It’s job would be to think about all of the information and this is where you may connect a dot. The job of this software would be to think about all of the information that represented what was going on in the enterprise at any given time as bank business was being transacted world-wide. For example, it would (act) as a surveillance software that looked for trading patterns that indicated that someone was up too no good and then do something about it: send a message somewhere, send transaction information somewhere, perhaps shut their system down, perhaps shut another system down, perhaps start something else up elsewhere. This type of capability is very, very essential in today’s world. However this kind of software is not found in Microsoft or not even in IBM. A small group of very esoteric software companies make this kind of enterprise software and it is very pricey. So you can’t afford to pick wrong and I asked all my colleagues who were industry gurus; what would they recommend for this? My buddies recommended PTech. (SOURCE: 9/11 Omission Hearings – Indira Singh Reads Sibel Edmonds’ Letter – 9/9/2004) Indeed, it’s not difficult to see why PTech came so highly recommended. Given the nature of this sensitive risk-management work, only a company with experience delivering software to large-scale organizations with secrets to protect would fit the bill, and in this regard PTech did not disappoint. Their client roster included a veritable who’s who of top-level corporate and governmental clients: the FBI, the IRS, NATO, the Air Force, the Naval Air Command, the Departments of Energy and Education, the Postal Service, the US House of Representatives, the Department of Defense, the Secret Service, even the White House. From the inner sanctum of the White House to the headquarters of the FBI, from the basement of the FAA to the boardroom of IBM, some of the best-secured organizations in the world running on some of the most-protected servers housing the most sensitive data welcomed PTech into their midst. PTech was given the keys to the cyber kingdom to build detailed pictures of these organizations, their weaknesses and vulnerabilities, and to show how these problems could be exploited by those of ill intent. But like all such systems, it could be exploited by those of ill intent for their own purposes, too. Given the nature of the information and secrets being kept by its clients, it should come as no surprise that many of PTech’s top investors and employees were men with backgrounds that should have been raising red flags at all levels of the government. And as it turns out, at least one of these men did raise red flags with a pair of diligent FBI field agents. In the late 1990s, Robert Wright and John Vincent—FBI special agents in the Chicago field office—were running an investigation into terrorist financing called Vulgar Betrayal. From the very start, the investigation was hampered by higher-ups; they were not even given access to the computer equipment needed to carry out their work. Through Wright and Vincent’s foresight and perseverance, however, the investigation managed to score some victories, including seizing $1.4 million in terrorist funds. According to Wright, “these funds were linked directly to Saudi businessman Yasin al-Qadi.” Yasin al-Qadi is a multi-millionaire businessman and philanthropist who, according to business associates, liked to boast of his relationship with former Vice President Dick Cheney. But in the late 1990s he was sanctioned by the UN Security Council for his suspected links to Al Qaeda, and after 9/11 he was put on a terrorist watch list by the US Treasury for his suspected ties to terrorist financing. During the 1990s, as Vulgar Betrayal was being thwarted from opening a criminal investigation into his activities, the Qadi-backed investment firm Sarmany Ltd. became an “angel investor” to a software startup called PTech, providing $5 million of the initial $20 million of capital that got PTech off the ground. At the time, PTech’s CEO denied that al-Qadi had any involvement with the company other than his initial investment, but the FBI now maintains he was lying and that in fact al-Qadi continued investing millions of dollars in the company through various fronts and investment vehicles. Company insiders told FBI officials that they were flown to Saudi Arabia to meet PTech’s investors in 1999 and that al-Qadi was introduced as one of the owners. It has also been reported that Hussein Ibrahim, PTech’s chief scientist, was al-Qadi’s representative at PTech and al-Qadi’s lawyers have admitted that al-Qadi’s representative may have continued to sit on PTech’s board even after 9/11. Ibrahim himself was a former president of BMI, a New Jersey-based real estate investment firm that was also one of the initial investors in PTech and provided financing for PTech’s founding loan. PTech leased office space and computer equipment from BMI and BMI shared office space in New Jersey with Kadi International, owned and operated by none other than Yassin al-Qadi. In 2003, counterterrorism czar Richard Clarke said: “BMI held itself out publicly as a financial services provider for Muslims in the United States, its investor list suggests the possibility this facade was just a cover to conceal terrorist support.” Suheil Laheir was PTech’s chief architect. When he wasn’t writing the software that would provide PTech with detailed operational blueprints of the most sensitive agencies in the U.S. government, he was writing articles in praise of Islamic holy war. He was also fond of quoting Abdullah Azzam, Osama Bin Laden’s mentor and the head of Maktab al-Khidamat, which was the precursor to Al-Qaeda. That such an unlikely cast of characters were given access to some of the most sensitive agencies in the U.S. federal government is startling enough. That they were operating software that allowed them to map, analyze and access every process and operation within these agencies for the purpose of finding systemic weak points is equally startling. Most disturbing of all, though, is the connection between PTech and the very agencies that so remarkably “failed” in their duty to protect the American public on September 11, 2001. BONNIE FAULKNER: Could you describe the relationship of PTech with the FAA? PTech worked with the FAA for several years, didn’t they? INDIRA SINGH: Yes. It was a joint project between PTech and MITRE. It is interesting. They were looking at, basically, holes in the FAA’s interoperability with responding with other agencies—law enforcement—in the case of an emergency such as a hijacking. They were looking for the escalation process—what people would do, how they would respond in case of an emergency—and find the holes and make recommendations to fix it. Now if anyone was in a position to understand where the holes were, PTech was, and that is exactly the point: if anybody was in a position to write software to take advantage of those holes, it would have been PTech. BONNIE FAULKNER: Was there a reference to PTech having operated in the basement out of the FAA? INDIRA SINGH: Yes. Typically, because the scope of such projects are so over-arching and wide-ranging, when you are doing an enterprise architecture project, you have access to how anything in the organization is being done, where it is being done, on what systems, what the information is. You have carte blanche. If it is a major project that spends several years, the team that comes in has, literally, access to almost anything that they want because you are operating on a blueprint level, on a massive scale. So, yes, they were everywhere, and I was told that they were in places that required clearances. I was told that they had log-on access to FAA flight control computers. I was told that they had passwords to many computers that you may not, on the surface, think has anything to do with finding out holes in the system, but let’s say you isolated part of a notification process that was mediated by computer and you wanted to investigate it further, then you would typically get log-on access to that computer. From that, back upstream or downstream. So, who knows? From my own experience I could have access to almost anything I wanted to in JP Morgan Chase. And did not, for the reason that if anything went wrong, I did not want to have the access. But if you were up to no good as an enterprise architect with such a mandate, you typically could have access to anything. (SOURCE: Guns n Butter: Indira Singh, PTech and the 911 software) So who was really behind PTech? Did Ziade, Ibrahim and the others somehow evade the due diligence of all of the government agencies and multinational corporations that PTech contracted with? Did PTech just happen to end up working on the interoperability of the FAA and the Pentagon systems on the morning of 9/11? Did al-Qadi’s friend Dick Cheney really know nothing of Qadi’s connections or activities? Was this all some devious Al Qaeda plot to infiltrate key systems and agencies of the US government? Not according to the people who were really investigating the company. INDIRA SINGH: Who’s really behind PTech is the question. Correct. I asked that of many intelligence people who came to my aid as I was being blacklisted and I was told: “Indira, it is a CIA clandestine operation on the level of Iran-Contra.” And I have reason to believe this because CARE International is a renamed version of Al Kifah, which was the finding arm for WTC 93, prior to Al Kifah it was called Maktab al-Khidamat which was the funding arms for the Afghani mujahidin. It was how the moneys got to Osama Bin-Laden through the Pakistani ISI. I asked the FBI in Boston: ‘”How come Mak was being run out of Ptech and 9/11?” and that jived with a lot of what intel was telling me that “it’s a CIA front, shut up and go away.” At that level I said “Well why doesn’t the FBI take advantage of their celebrated difference with the CIA’ and I was told ‘because at that level they work together.” (SOURCE: 9/11 Omission Hearings – Michael Ruppert & Indira Singh Q&A – 9/9/2004) So what did the 9/11 Commission have to say about PTech? Absolutely nothing. The co-chair of the commission, Thomas Kean, had been involved in a $24 million real estate transaction with BMI, one of the PTech investors, but no mention was made of that at the time and the Commission never looked into PTech or its activities on 9/11. Meanwhile, Cheney’s friend al-Qadi has since been removed from the Swiss, European, UN Security Council and US Treasury terrorist sanctions lists. And Robert Wright? After Vulgar Betrayal was shut down, the FBI did eventually raid PTech’s offices in December 2002…but not before the company was given advance warning of the “raid.” The very next day then-Homeland Security chief Tom Ridge declared that PTech “in no way jeopardizes the security of the country.” Oussama Ziade is still wanted by the FBI for lying about al-Qadi’s involvement with the company, but the case is now cold. ROBERT WRIGHT: To the families and victims….of September 11th…on behalf of John Vincent, Barry Carnaby and myself…we’re sorry. (SOURCE: 9-11 FBI Whistleblower Robert Wright Testimony) The Pentagon’s Missing Trillions DONALD RUMSFELD: The topic today is an adversary that poses a threat, a serious threat, to the security of the United States of America. This adversary is one of the world’s last bastions of central planning. It governs by dictating five-year plans. From a single capital, it attempts to impose its demands across time zones, continents, oceans and beyond. With brutal consistency, it stifles free thought and crushes new ideas. It disrupts the defense of the United States and places the lives of men and women in uniform at risk. (SOURCE: Defense Business Practices) On September 10, 2001, Defense Secretary Donald Rumsfeld declared a new war. Not a war on a shadowy terrorist organization in Afghanistan, or even a war on terror, but a war on the Pentagon itself. DONALD RUMSFELD: The adversary is closer to home. It’s the Pentagon bureaucracy. (SOURCE: Defense Business Practices) Perhaps it is no surprise that Rumsfeld felt compelled to declare a war on the Pentagon’s bureaucracy. The issue of the Pentagon’s $2.3 trillion accounting nightmare had been dogging him since his confirmation hearings in January of 2001. Although Rumsfeld was interested in pushing forward a modernization of the military that was projected to cost an additional $50 billion in funding, that agenda was politically impossible in the face of the Department of Defense’s monumental budget problem. SEN. BYRD: How can we seriously consider a $50 billion increase in the Defense Department budget when DoD’s own auditors—when DoD’s own auditors—say the department cannot account for $2.3 trillion in transactions in one year alone. Now, my question to you is, Mr. Secretary, what do you plan to do about this? DONALD RUMSFELD: Decline the nomination! (Laughs.) (Laughter.) Ah! Senator, I have heard -- SEN. BYRD: I don’t want to see you do that! (Laughter.) SEN. LEVIN: (Sounds gavel.) We’ll stand adjourned, in that case! (Laughter.) DONALD RUMSFELD: Senator, I have heard some of that and read some of that, that the department is not capable of auditing its books. It is — I was going to say “terrifying.” (SOURCE: Defense Secretary Nomination Hearing Jan 11 2001) “Terrifying” only begins to describe the problem. The Department of Defense’s own Inspector General report for Fiscal Year 1999 noted that the Defense Finance and Accounting Service had processed $7.6 trillion of department-level accounting entries in that year. Of that amount, only $3.5 trillion could be properly accounted for. $2.3 trillion in transactions were fudged to make entries balance, run through without proper documentation, or made up entirely. The Inspector General’s office did not even examine the other $1.8 trillion in transactions because they “did not have adequate time or staff to review” them. In 2002 one DFAS accountant blew the whistle on the problem and the cover-up that was underway to stop investigators from finding out where the money went. VINCE GONZALES: $2.3 trillion with a “T.” That’s 8,000 dollars for every man, woman and child in America. To understand how the Pentagon can lose track of trillions, consider the case of one military accountant who tried to find out what happened to a mere $300 million. JIM MINNERY: We know it’s gone, but we don’t know what they spent it on. VINCE GONZALES: Jim Minnery, a former Marine turned whistleblower, is risking his job by speaking out for the first time about the millions he noticed were missing from one defense agency’s balance sheets. Minnery tried to follow the money trail, even crisscrossing the country looking for records. JIM MINNERY: The director looked at me and said, “Why do you care about this stuff?” That took me aback, you know. My supervisor asked me why I care about doing a good job. VINCE GONZALES: He was reassigned, and says officials then covered up the problem by just writing it off. JIM MINNERY: They’ve got to cover it up. (SOURCE: 9-11 Pentagon missing $2.3 trillion) As Comptroller of the Pentagon from 2001 to 2004, Dov Zakheim was the man tasked with solving this problem. DONALD RUMSFELD: There are all kinds of long-standing rules and regulations about what you can do and what you can’t do. I know Dr. Zakheim’s been trying to hire CPAs because the financial systems of the department are so snarled up that we can’t account for some $2.6 trillion in transactions that exist, if that’s believable. And yet we’re told that we can’t hire CPAs to help untangle it in many respects. REP. LEWIS: Mr. Secretary, the first time and the last time that Dov Zackheim and I broke bread together, he told me he would have a handle on that 2.6 trillion by now. (Laughter.) But we’ll discuss that a little -- DONALD RUMSFELD: He’s got a handle; it’s just a little hot. (Laughter.) (SOURCE: Testimony before the House Appropriations Committee: FY2002 Budget Request) From 1987 to 2001, Zakheim headed SPC International, a subsidiary of System Planning Corporation, a defense contractor providing airwarfare, cybersecurity and advanced military electronics to the Department of Defense and DARPA. SPC’s “Radar Physics Laboratory” developed a remote control system for airborne vehicles that they were marketing to the Pentagon prior to 9/11. Zakheim was also a participant in drafting “Rebuilding America’s Defenses,” a document that called for a sweeping transformation of the US military, including the implementation of the $50 billion missile defense program and increased use of specialized military technologies. The paper even noted how “advanced forms of biological warfare that can target specific genotypes may transform biological warfare from the realm of terror to a politically useful tool.” “Rebuilding America’s Defenses” was a white paper produced by the Project for a New American Century, a group founded in 1997 with the goal of projecting American global dominance into the 21st century. Joining Zakheim in the group were a host of other neocons who ended up populating the Bush administration, including Dick Cheney, Paul Wolfowitz, Richard Perle, Jeb Bush, and Donald Rumsfeld. In their September 2000 document, the group lamented that their plan for transforming the military was not likely unless a defining event took place, one that would galvanize public opinion: “[T]he process of transformation, even if it brings revolutionary change, is likely to be a long one, absent some catastrophic and catalyzing event—like a new Pearl Harbor.” DONALD RUMSFELD: We know that the thing that tends to register on people is fear, and we know that that tends to happen after there’s a Pearl Harbor, tends to happen after there’s a crisis. And that’s too late for us. We’ve got to be smarter than that. We’ve got to be wiser than that. We have to be more forward-looking. There’s a wonderful book on Pearl Harbor by Roberta Wohlstetter, and a forward by Dr. Schelling, that talks about this problem of seeing things happen and not integrating them in your mind and saying, “Yes, we need to be doing something about that now,” that I reread periodically because it’s so important. (SOURCE: Defense Secretary Nomination Hearing Jan 11 2001) And on 9/11/2001, America received its new Pearl Harbor. The attack on the Pentagon struck Wedge One on the west side of the building. An office of the U.S. Army called Resource Services Washington had just moved back into Wedge One after renovations had taken place there. The office was staffed with 45 accountants, bookkeepers and budget analysts; 34 of them were killed in the attack. A 2002 follow-up report from the DoD Inspector General on the missing trillions noted that a further $1.1 trillion in made up accounting entries were processed by the Pentagon in fiscal year 2000, but they did not even attempt to quantify the missing funds for 2001. The Secretary of the Army, Thomas White, later explained they were unable to produce a financial report for 2001 at all due to “the loss of financial-management personnel sustained during the Sept. 11 terrorist attack.” Before becoming Secretary of the Army, Thomas White was a senior executive at Enron. Enron was one of the largest energy companies in the world, posting a $111 billion profit in 2000 before being exposed as an elaborate corporate accounting fraud in 2001. The SEC, which investigated the Enron scandal, occupied the 11th to 13th floors in World Trade Center Building 7, and their offices were destroyed on 9/11, destroying 3,000 to 4,000 documents on active investigations in the process. Perhaps unsurprisingly, Rumsfeld’s War on the Pentagon’s Bureaucracy did not yield the results he promised. By 2013, the unaccountable money in the Pentagon’s coffers had reach $8.5 trillion. REPORTER: The latest scandal to hit Washington comes from a report revealing the Pentagon “misplaced” $8.5 trillion. Military leaders have also been found ordering subordinates to doctor books to hide the missing money. This is the conclusion of a special report by Reuters. One former Pentagon employee, Linda Woodford, said she spent 15 years there falsifying financial records. Woodford had a job checking Navy accounting records against figures supplied by the Treasury Department. She said money was missing from the report every month. (SOURCE: $8.5 Trillion Missing From Pentagon Budget) GAYANE CHICHAKYAN: National security expert Steve Miles is here with me to help us crunch these numbers. $8.5 trillion unaccounted for? STEPHEN MILES: That’s a lot of money. This is the kind of thing that you would think would bring Capitol Hill to a screeching halt. There’d be hearings almost every day. You’d have various committees looking into it. None of that. It just leads to massive waste and there can be all sorts of fraud that you don’t know about. Just one example, when the Inspector General looked at Iraq — which was a lot of money, but in the grand scheme just a portion of the money the U.S. spent — what they found was about $50 billion of the money the U.S. spent there was wasted and about $6 billion was completely lost. They had no idea where it went, it was completely unaccounted for. Put that in perspective. That’s about the amount of money that other countries would spend on their defense, total. And that’s just the loose pocket change that we lost in the couch. GAYANE CHICHAKYAN: One thing I found very interesting in this report is that the Pentagon apparently uses standard operating procedure to enter false numbers, or so-called “plugs,” to cover lost or missing information in their accounting in order to submit a balanced budget to the Treasury. So they can write in everything. STEPHEN MILES: This is probably the most shocking part of this. They get to the end of the day and they say, “Oh, there’s money missing, what do we do?” “Well, we’ll just put a number in there that says it’s there and we’ll sort it out later.” Again this is the type of operating practice that if you did it in your own business—if you try to do it with your own taxes for the government—they’d haul you off to jail. (SOURCE: Black Budget: US govt clueless about missing Pentagon $trillions) But then, given that the trillions have never been accounted for, and given that American defense spending soared to record levels after the attack, perhaps Rumsfeld’s war on the Pentagon, the one he announced on September 10th, was successful after all. And perhaps September 11th was the key battle in that war. DONALD RUMSFELD: Some might ask, how in the world could the Secretary of Defense attack the Pentagon in front of its people? To them I reply, I have no desire to attack the Pentagon; I want to liberate it. (SOURCE: Defense Business Practices) No Conclusion Insurance scams and insider trading, electronic fraud and Vulgar Betrayal, missing money and evidence destroyed. There are at least 8.5 trillion reasons to investigate the money trail of 9/11. Curious, then, that the US government’s final word on the attacks, the 9/11 Commission Report, concluded that the money trail was not worthy of investigation at all. In Chapter Five of the report, the commission noted: “To date, the U.S. government has not been able to determine the origin of the money used for the 9/11 attacks. Ultimately the question is of little practical significance.” 9/11 was a crime. And as every detective knows, the first rule of criminal investigation is to follow the money. So why did the 9/11 Commission specifically reject this rule? The answers to 9/11 are not going to come from the suspects of the crime. Instead, it’s up to investigators to continue to unearth the true evidence on the 9/11 money trail. Follow the money… |
This feed contains research, news, information, observations, and ideas at the level of the world.
Archives
May 2024
Categories
All
|
||||||||||||||||||||||







 RSS Feed
RSS Feed

