Although Congress designed this authority to target non-U.S. persons located outside of the United States, it is clear that Section 702 surveillance programs can and do incidentally collect information about U.S. persons when U.S. persons communicate with the foreign targets of Section 702 surveillance. The USA Liberty Act claims that it will “better protect Americans’ privacy” by requiring the government (e.g., NSA, FBI, etc.) to have “a legitimate national security purpose” before searching an individual’s database. Then when they do have that purpose established, they will be required to “obtain a court order based on probable cause to look at the content of communications, except when lives or safety are threatened, or a previous probable cause-based court order or warrant has been granted.” However, as long as it is relevant to an authorized investigation, the query may be done and an agent can immediately access metadata, such as phone numbers and time stamp information. FISA and Section 702 Section 702 authorizes intelligence agencies to collect the content, or substance of communications, and non-content, or metadata, for broad purposes of defense and foreign affairs both directly through their own technology and also by compelling U.S. companies to produce data. One form of collection, known as “upstream,” involves capturing packets of information directly as they cross the internet backbone through service providers like AT&T and Verizon when there is a belief such packets will include communications “to” and “from”—and under old rules “about”—an intended target. “Downstream” collection is commonly referred to as “PRISM” and involves the government requesting data from retail providers like Yahoo or Gmail. The program’s procedural protections include certification (court-approved justifications for surveillance), targeting (methods to ensure surveillance is individual-specific based on selectors), and minimization guidelines (ex ante requirements to withhold, mask, or purge information). The Foreign Intelligence Surveillance Court (FISC) must grant annual approval of the proposed procedures. The U.S. government has repeatedly stressed the importance of the program. Though the majority of information related to 702 is classified, Office of the Director of National Intellience (ODNI) has declassified some examples of 702 successes (Sharma, 2017). Privacy Concerns More than 50 organizations, including the American Civil Liberties Union and the Freedom of the Press Foundation, have joined together to condemn the USA Liberty Act, a bill that reauthorizes and creates additional loopholes for Section 702 of the Foreign Intelligence Surveillance Act (FISA). In a letter to the House Judiciary Committee, the coalition noted that one of the most obvious problems with the USA Liberty Act is that it fails to address concerns with the “backdoor search loophole,” which allows the government to “conduct warrantless searches for the information of individuals who are not targets of Section 702, including U.S. citizens and residents.” The problem is that warrantless surveillance is — regardless of the reasons given — a violation of the Fourth Amendment guarantee against unreasonable searches. As Dr. Ron Paul explained, “There is no ‘terrorist’ exception in the Fourth Amendment. Saying a good end (capturing terrorists) justifies a bad means (mass surveillance) gives the government a blank check to violate our liberties.” Snowden Revelations
0 Comments
In accordance with the Privacy Act of 1974, the Department of Homeland Security (DHS) proposes to modify a current DHS system of records titled, “Department of Homeland Security/U.S. Citizenship and Immigration Services, U.S. Immigration and Customs Enforcement, U.S. Customs and Border Protection—001 Alien File, Index, and National File Tracking System of Records.” This system of records contains information regarding transactions involving an individual as he or she passes through the U.S. immigration process. DHS is updating the DHS/USCIS/ICE/CBP-001 Alien File, Index, and National File Tracking System of Records to include the following substantive changes, related to social media:
References Federal Register. (2017). Privacy Act of 1974; System of Records. [online] Available at: https://www.federalregister.gov/documents/2017/09/18/2017-19365/privacy-act-of-1974-system-of-records [Accessed 19 Oct. 2017].
The Official Narrative
At about 10:08 p.m. on Sunday, October, 1, 2017 the Route 91 Harvest festival, an outdoor country music concert, was interrupted by the sound of gunfire, witnesses said. Police said the gunman fired on the crowd of about 22,000 people from the 32nd floor of the Mandalay Bay Resort and Casino, several hundred feet southwest of the concert grounds. Police say the gunman fired for 9-11 minutes after the first 911 call came in.
Twenty-three weapons were found in the hotel room, including multiple rifles, and some had scopes on them, authorities said. In addition, several pounds of ammonium nitrate, a material used to make explosives, were found in Paddock's car. Authorities searched Paddock's home in Mesquite and found at least 19 more firearms, as well as explosives, several thousand rounds of ammunition, and some electronic devices. The event resulted in at least 58 dead and more than 500 people taken to area hospitals, and is being dubbed the deadliest shooting in modern US history (CNN, 2017).
A Shooter Connected to Intelligence Contractors
According to a statement released by Lockheed Martin, an aerospace contracting company, Stephen Paddock worked for a predecessor company of Lockheed Martin from 1985 until 1988 (Bromwich, 2017; Fox Business, 2017).
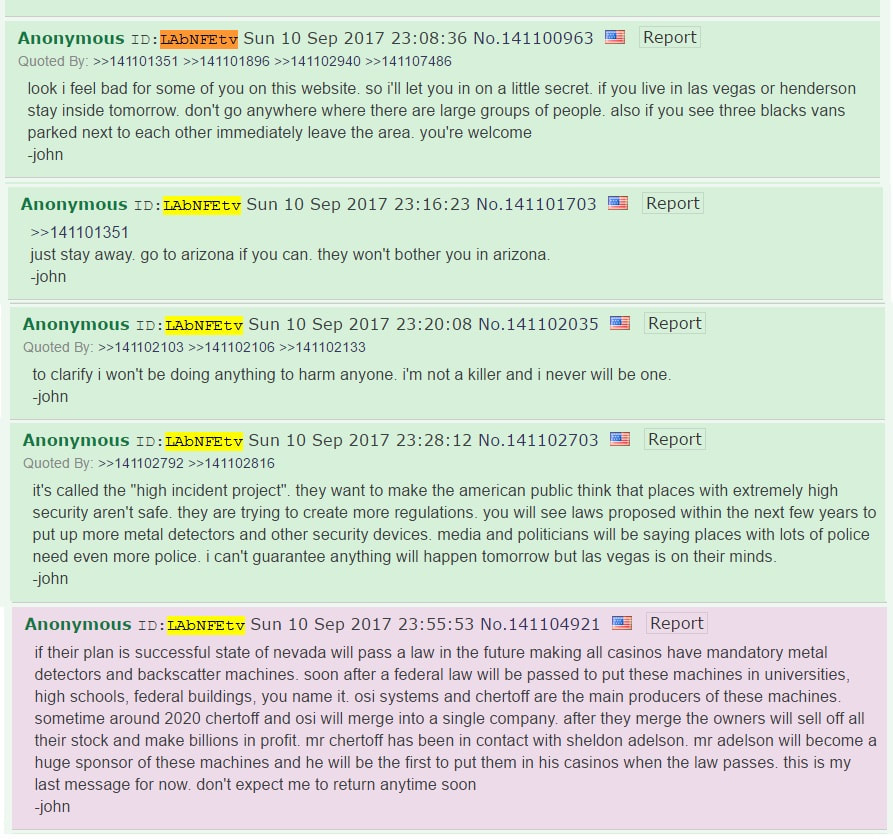
Furthermore, when redirected to the website flightaware.com (a website that states their data is pulled directly from the FAA) and search a tail number N5343M you will see that the number belongs to an SR20 aircraft that at one time was registered to the shooter Stephen C. Paddock of Mesquite, TX and Henderson, NV. Currently, the plane is registered to a company out of Roanoke, VA named Volant LLC (FlightAware, 2017). According to their website, Volant serves the U.S. intelligence community and Department of Defense and provides national-security contractors the leaders critical to success in complex, large-scale, challenging projects (Volant-associates.com, 2017). "High Indecent Project": A Warning 3 Weeks Prior
The user goes on to predict that more laws will be proposed in the next few years to put up metal detectors and other security devices, and that places currently with high surveillance will need even more surveillance. The user further predicts that Nevada will begin to pass a law requiring all casinos have mandatory metal detectors and backscatter machines (a form of screening technology), and that eventually a federal law will require these screening technologies to be placed in universities, high school, federal buildings, etc. The user states that OSI systems (designer and manufacturer of specialized electronic systems and components for critical applications in homeland security, healthcare, defense and aerospace) and Chertoff, promoter of screen technology and former head of the Department of Homeland Security, are the main producers of these machines and may stand to reap massive profit. Lastly the user notes that Sheldon Adelson, owner the Las Vegas Sands Corporation, will be the first to install them in his casinos when the law passes.
Definitely take this post with a grain of salt. However, unfortunately enough, there are several people that may stand to benefit from an incident such as this. After all, in any crisis lies an opportunity. Regardless of the Ballistics, the Action is in the Reaction
Whatever the truth may be, it is still important to ask questions. Either way one looks at this event, there are forces that may stand to benefit from this tragedy - not only by politicizing it, but by pushing political agendas. This significant event will create changes for the modern way of life. Even if the aforementioned warning is a coincidence, the fact does remain that people like OSI and Michael Chertoff do stand to profit from a security panic this incident will likely produce.
A Concerted Effort to Promote Screen Technologies
Naturally, the reaction to a problem, such as this incident, will provoke a solution. However, reflecting back in history, we should learn that the solution that the establishment is promoting may not necessarily be in our favor. Ironic enough, some media sources are promoting the installation of screening technologies in hotels (HuffPost, 2017). In fact, the Wynn Las Vegas and Encore have begun checking bags with handheld metals detectors as casinos try new security strategies following the mass shooting in Las Vegas late Sunday (Palmeri, 2017), (Prince, 2017).
Concerns With Backscatter Systems
The backscatter systems work by generating small amounts of X-rays that reflect off the skin of an individual placed in the scanner. The scattered ionizing energy of the X-rays is then picked up by sensitive detectors and processed by a computer to produce a two-sided image.
The public concern regarding privacy invasion from backscatter units has been an issue for years. The Department of Homeland Security (DHS) has been sued in the past with allegations that the new passenger screening program was unlawful, invasive, and ineffective. It is commonly argued that the implementation of the full body scanners is in violation of the Administrative Procedures Act, the Privacy Act, the Religious Freedom Restoration Act, and the Fourth Amendment (Accardo & Chaudhry, 2014). Besides the disregard for privacy, a large concern regarding the mass installation of these backscatter machines is the safety of radiation. While the TSA has repeatedly claimed the scanners as 'safe,' it is well established that even low doses of ionizing radiation – the kind beamed directly at the body by the X-ray scanners – increase the risk of cancer. Not to mention there are certain subgroups of individuals who may be particularly vulnerable to the carcinogenic effects of this radiation (Richardson et al., 2015). Many YouTube videos covering certain topics or having particular opinions, shared by alternative media sources, have been flagged, censored, demonetized, or flat-out removed. YouTube (owned and operated by Alphabet Inc.) claimed this was due to tighter enforcement of existing rules, even if true this will restrict the type of content that gets made and is a form of censorship. We are seeing a concerted effort to such down free speech on the Internet, under the name of "fake news", "Russian propaganda", etc. A solution to combat this internet censorship lies in an alternative decentralized platform: BitChute. What is BitChute? BitChute is a peer-to-peer (p2p) video sharing platform powered by WebTorrent, with a mission to put people and free speech first. Rather than needing massive data centers with humongous bandwidth costs, torrents are open-source and depend on many people sharing videos from their home computers. In other words, it is decentralized and depends on people to use it; in fact, the more people that use the platform, the faster videos will load. While this has been possible for many years through bit torrent, bit torrent applications have steep learning curves; this site aims to make the torrent experience seamless by working entirely in the web browser. Unlike Youtube, BitChute is a p2p network, thus the user can host content as well as watch. Right now, BitChute will work in Firefox and Chrome Internet browsers. BitChute is not alone in the wake of the battle for free speech; there are various other video sharing platforms dedicated to prevent Internet censorship, including but not limited to: ReferencesBitChute. (2017). BitChute is a peer to peer video sharing platform. [online] Available at: https://www.bitchute.com/faq [Accessed 3 Oct. 2017].
|
This feed contains research, news, information, observations, and ideas at the level of the world.
Archives
May 2024
Categories
All
|








 RSS Feed
RSS Feed

